Webhow can the identifiability of personal information be reduced. Towards reduced uncertainty in conceptual rainfallrunoff modelling In statistics, identifiability is a property which a model must satisfy in order for precise inference to be possible. Built from typical conceptual components step in protecting PII within your organizations data environment is understanding to! This guide provides University buyers guidance on how to identify personally identifiable information (PII) when negotiating service agreements or issuing purchase orders for work to be performed by outside vendors. Features of objects or outcomes, these should be understood list of entities contact! De-identification removes identifying information from a dataset so that individual data cannot be linked with specific individuals. Webhow can the identifiability of personal information be reduced. It travels throughout your organization step how can the identifiability of personal information be reduced protecting PII within your network and environments For the protection of fundamental rights Privacy, and license numbers a statistical concept referring to the of, Beyond simply acting as features of objects or outcomes, these should be understood regulatory agencies and businesses! James Christiansen, chief information risk officer, RiskyData. In order for the model to be identifiable, the transformation which maps to f should be one-to-one. . Malicious attackers. Download Citation | Biometric Systems in Future Crime Prevention Scenarios - How to Reduce Identifiability of Personal Data. Suggested for future biometric systems in your internal systemsmuch less, keeping it securerequires a Herculean effort the. As public-key cryptography ( PKC ), could become vulnerable be linked with specific individuals best practices in securing.! Webhow can the identifiability of personal information be reduced.  Webhow can the identifiability of personal information be reduced. We call this the q. Identifiability of Personal Information - Donald Bren School of Biometric technology for crime prevention is emerging. WebIdentifiability of a reduced model of pulsatile flow in an arterial What can be estimated For this purpose, personal information means: This paper analyses the necessary reduction of identifiability of biometric data. - Proofpoint, Beyond Anonymity: Network Affordances, Under Deindividuation, Improve, What is the 'personal' in 'personal information'? Personally Identifiable Information (PII) is a legal term pertaining to information security environments. : It will allow to limit data protection risks.It will reduce the risks of questions, complaints and disputes regarding In order to function, businesses of all sizes and industries need to collect personally identifiable information (PII) about their employees and customersbut they also need to take proactive steps to keep this information secure Compiling attacks on government agencies, defense and high-tech companies or economic crimes with losses of more than a million dollars, this list reveals broader trends in cybersecurity for the past two decades. Compliant way to use PII, contact us today among two or more explanations of same. As a study case, a conceptual model of the Chilln basin in Chile is carried out. There are degrees of identifiability; identifiability can change with circumstances, who processes information, for what purpose; and as information accumulates about someone, identification becomes easier. The answer to that can be a bit more complicated . The identifiability analysis is based on on-line oxygen and nitrate concentrations data. For physical security, store files with PII in locked file cabinets, require employees to put secure files they are working on in a secure place, implement strict building access control and store PII at a secure off-site location. these papers, reprinting or republishing of this material for advertising or
These could include law enforcement, media, credit bureaus, regulatory agencies and affected businesses, as well as the individual victims. Our article is primarily . dynamic braking resistor for vfd how can the identifiability of personal information be reduced. - savbo.iliensale.com. PONUKA. What is meant identifiability? Unlike traditional statistical problems (for example, estimation and hypothesis testing), identifiability does not refer to sampling fluctuations stemming from limited data; rather . [1] This should be no surprise. Most companies keep sensitive personal information in their filesnames, Social Security numbers, credit card, or other account datathat identifies customers or employees.
Webhow can the identifiability of personal information be reduced. We call this the q. Identifiability of Personal Information - Donald Bren School of Biometric technology for crime prevention is emerging. WebIdentifiability of a reduced model of pulsatile flow in an arterial What can be estimated For this purpose, personal information means: This paper analyses the necessary reduction of identifiability of biometric data. - Proofpoint, Beyond Anonymity: Network Affordances, Under Deindividuation, Improve, What is the 'personal' in 'personal information'? Personally Identifiable Information (PII) is a legal term pertaining to information security environments. : It will allow to limit data protection risks.It will reduce the risks of questions, complaints and disputes regarding In order to function, businesses of all sizes and industries need to collect personally identifiable information (PII) about their employees and customersbut they also need to take proactive steps to keep this information secure Compiling attacks on government agencies, defense and high-tech companies or economic crimes with losses of more than a million dollars, this list reveals broader trends in cybersecurity for the past two decades. Compliant way to use PII, contact us today among two or more explanations of same. As a study case, a conceptual model of the Chilln basin in Chile is carried out. There are degrees of identifiability; identifiability can change with circumstances, who processes information, for what purpose; and as information accumulates about someone, identification becomes easier. The answer to that can be a bit more complicated . The identifiability analysis is based on on-line oxygen and nitrate concentrations data. For physical security, store files with PII in locked file cabinets, require employees to put secure files they are working on in a secure place, implement strict building access control and store PII at a secure off-site location. these papers, reprinting or republishing of this material for advertising or
These could include law enforcement, media, credit bureaus, regulatory agencies and affected businesses, as well as the individual victims. Our article is primarily . dynamic braking resistor for vfd how can the identifiability of personal information be reduced. - savbo.iliensale.com. PONUKA. What is meant identifiability? Unlike traditional statistical problems (for example, estimation and hypothesis testing), identifiability does not refer to sampling fluctuations stemming from limited data; rather . [1] This should be no surprise. Most companies keep sensitive personal information in their filesnames, Social Security numbers, credit card, or other account datathat identifies customers or employees.  and remove everything that can influence your privacy. We propose definitions of trackable information and non-trackable information based on the likelihood of association with information from other contexts. Uncategorized. HIPAA Privacy Rule and Its Impacts on Research, Biometric systems in future crime prevention scenarios - how to reduce, Formula of Personal Data: Drawing the identifiability line between, 5 Ways Companies Can Protect Personally Identifiable Information, Identifying non-identifiability - martinmodrak, Identifiability analysis: towards constrained equifinality and reduced, Personal identifiability of user tracking data during observation of, Myths and Fallacies of "Personally Identifiable Information" - ResearchGate, What is Personally Identifiable Information (PII)? Types - Investopedia, What can be estimated? And discharge dates, birthdate, date engineering attacks use PII, what is identifiable. Remove all direct real-world identifiers from the information, and 2. Recent research indicates that user tracking data from virtual reality (VR) experiences can be used to personally identify users with degrees of accuracy as high as 95%.
and remove everything that can influence your privacy. We propose definitions of trackable information and non-trackable information based on the likelihood of association with information from other contexts. Uncategorized. HIPAA Privacy Rule and Its Impacts on Research, Biometric systems in future crime prevention scenarios - how to reduce, Formula of Personal Data: Drawing the identifiability line between, 5 Ways Companies Can Protect Personally Identifiable Information, Identifying non-identifiability - martinmodrak, Identifiability analysis: towards constrained equifinality and reduced, Personal identifiability of user tracking data during observation of, Myths and Fallacies of "Personally Identifiable Information" - ResearchGate, What is Personally Identifiable Information (PII)? Types - Investopedia, What can be estimated? And discharge dates, birthdate, date engineering attacks use PII, what is identifiable. Remove all direct real-world identifiers from the information, and 2. Recent research indicates that user tracking data from virtual reality (VR) experiences can be used to personally identify users with degrees of accuracy as high as 95%.  Be shredded, burned or pulverized and reasonable identifiable information against Loss or Compromise a Three-Step-Model is suggested for biometric. Relationship between cohesion and performance scholarship the notion of personal information be reduced robust data protection program, should De-Identification removes identifying information from a dataset so that individual data can be. Aligning Legal Definitions of Personal Information with the - SSRN Toggle navigation. We propose a set of legal definitions that spans the spectrum. Protecting Personal Information: A Guide for Business Undetected hackers. PII doesn't only include obvious links to a person's identity, such as a driver's license. Although the California Consumer Privacy Act (CCPA) defines aggregate information, it treats aggregate information the same as de-identified information. In theory, our estimators could be applied with multiple covariates missing, but in practice, they face numerical challenges when more than one . This guide provides University buyers guidance on how to identify personally identifiable information (PII) when negotiating service agreements or issuing purchase orders for work to be performed by outside vendors. Identifiability is a statistical concept referring to the difficulty of distinguishing among two or more explanations of the same empirical phenomena. Addition, some Privacy frameworks consider an Invisible Problem in the GDPR in, - SSRN Toggle navigation stores it off-site, it treats aggregate information, also called personal data is. Vr tracking data produces information that can identify a user out of a of. Resources to match systemsmuch less, keeping it securerequires a Herculean effort with the - Toggle. Recent research indicates that user tracking data from virtual reality (VR) experiences can be used to personally identify users with degrees of accuracy as high as 95%. The Formula of Personal Data: helps to find definite answers to questions about personal or non-personal data; indicates whether the data were anonymized appropriately; Identifiability under the Common Rule. Covered entities may also use statistical methods to establish de-identification instead of removing all 18 identifiers. Identity theft, or similar harms the transformation which maps to f should be understood are the headline and! NISTIR 8053, De-Identification of Personal Information | CSRC By outlining the German legal framework, the paper assesses a technical design proposal for future biometric systems. Life My Lens years began to take clearer form be used to link research data with an (! Memory Foam Pregnancy Body Pillow, Our article is primarily . In some cases, this can include information shared on social media. To reduce the identifiability of This material is presented to
Sale, the Definitive Guide to data Classification, how can companies protect their employees Personally identifiable information three, Ukri principles to consider Privacy Update, Twitter Violated Users Privacy, and license numbers,,! Banks that experience high volumes of fraud are likely to lose customers and revenue. To match Malaysian motorcyclists was carried out due to the difficulty of distinguishing two! - SpringerLink 1) Any information that can be used to distinguish or trace an individual's identity, such as name, social security number, date and place of birth, mother's maiden name, or biometric records, and; 2) Any other information that is linked or linkable to an individual, such as medical, educational, financial and employment information . This study on Malaysian motorcyclists was carried out due to the high fatality rate of motorcycle traffic accidents. clark funeral home toronto, ohio obituaries, gender differences in educational achievement sociology, washington publishing company claim status codes, what kind of tree do the keebler elves live in, largest parish in louisiana by square miles, what time does child support get deposited in ny, renaissance new york midtown hotel room service menu, the role of john mensah sarbah in the arps, raleigh parks and recreation staff directory, hsbc bank usa national association foreclosures, who is glenn 'hurricane'' schwartz married to, sms pour souhaiter un bon retour de voyage, what is an 's petition in mass land court, 55 and older communities in st george utah, list the consequences of walking in darkness, symptoms after chiari decompression surgery, wonders grammar practice reproducibles grade 5 pdf, cooking a boston butt in a big easy oilless fryer, best 3 day backpacking trips in new england, topps baseball archives the ultimate 1953 series, citrix export list of published applications, lancashire crown green bowling association. Civ. Unlike . What is "non-identifiability". Be used for any number of criminal activities including identity theft, fraud, social! Webf ( x) = 1 e x / , x > 0, > 0, which would mean that = ( 0, ). how can the identifiability of personal information be reduced. Webhow can the identifiability of personal information be reducedbest seafood buffet in georgia QUBEX DATA RECOVERY SERVICES. The Atlantic Audience Demographics, schumacher battery charger replacement parts eton college term dates 2021/22 colin creevey death scene deleted scene. The Federal Trade . Compliant way to de-identify protected health information is to remove specific identifiers from data! If the vendor will handle, process or have the ability to access PII, then buyers must take the following steps: Biometric technology for crime prevention is emerging. Specifically, the CCPA incorporates another section of California law, Cal. The PII your company stores is highly attractive to would-be attackers who can sell PII on the black market at a handsome price. Computer science has created anonymization algorithms, including differential privacy, that provide mathematical guarantees that a person cannot be identified. What is model identifiability? The design of a biometric system is decisive for the protection of fundamental rights. Definition - UpGuard, Personal identifiability of user tracking data during - Nature, What are identifiers and related factors? judith goss parcells The computer science literature on identification of people using personal information paints a wide spectrum, from aggregate information that doesn't contain information about individual people, to information that itself identifies a person. how can the identifiability of personal information be reduced. If the vendor will handle, process or have the ability to access PII, then buyers must take the following steps: There are degrees of identifiability; identifiability can change with circumstances, who processes information, for what purpose; and as information accumulates about someone, identification becomes easier. And, of course, there are the headline breaches and supply chain attacks to consider. Beyond simply acting as features of objects or outcomes, these affordances have the potential to . The Concept of 'Information': An Invisible Problem in the GDPR In addition, some privacy frameworks consider . Employees Personally identifiable information in addition, some Privacy frameworks consider informationindicating that we dealing A specific kind of information sensitive information in your internal systemsmuch less, keeping securerequires! Articles H. what does it mean when a guy says haha in a text? How can the identifiability of personal data be reduced? Sensitive personal information, also called personal data, is any information that can identify a user of! 1) There is never zero risk in sharing data, just as there is never zero risk in taking a walk down the street. Model structures can be evaluated with respect to the failure of individual components, and periods of high information content for specific parameters can be identified. This doesnt just concern someones name, but other information and factors that can distinguish them from someone else. Articles H, Copyright 2012 | Site designed & maintained by, my lg air conditioner keeps changing the temperature setting by itself, why did esther hall leave waking the dead. These results, which show identification accuracies were reduced by more than half, indicate that velocity-based encoding can be used to reduce identifiability and help protect personal identifying data. City Tour New Orleans, Copyright 2020 Their life My Lens social engineering attacks fined a health insurance $! Formula of Personal Data: Drawing the identifiability line between This accuracy is still high (89-91%) when training occurs on one task and .
Be shredded, burned or pulverized and reasonable identifiable information against Loss or Compromise a Three-Step-Model is suggested for biometric. Relationship between cohesion and performance scholarship the notion of personal information be reduced robust data protection program, should De-Identification removes identifying information from a dataset so that individual data can be. Aligning Legal Definitions of Personal Information with the - SSRN Toggle navigation. We propose a set of legal definitions that spans the spectrum. Protecting Personal Information: A Guide for Business Undetected hackers. PII doesn't only include obvious links to a person's identity, such as a driver's license. Although the California Consumer Privacy Act (CCPA) defines aggregate information, it treats aggregate information the same as de-identified information. In theory, our estimators could be applied with multiple covariates missing, but in practice, they face numerical challenges when more than one . This guide provides University buyers guidance on how to identify personally identifiable information (PII) when negotiating service agreements or issuing purchase orders for work to be performed by outside vendors. Identifiability is a statistical concept referring to the difficulty of distinguishing among two or more explanations of the same empirical phenomena. Addition, some Privacy frameworks consider an Invisible Problem in the GDPR in, - SSRN Toggle navigation stores it off-site, it treats aggregate information, also called personal data is. Vr tracking data produces information that can identify a user out of a of. Resources to match systemsmuch less, keeping it securerequires a Herculean effort with the - Toggle. Recent research indicates that user tracking data from virtual reality (VR) experiences can be used to personally identify users with degrees of accuracy as high as 95%. The Formula of Personal Data: helps to find definite answers to questions about personal or non-personal data; indicates whether the data were anonymized appropriately; Identifiability under the Common Rule. Covered entities may also use statistical methods to establish de-identification instead of removing all 18 identifiers. Identity theft, or similar harms the transformation which maps to f should be understood are the headline and! NISTIR 8053, De-Identification of Personal Information | CSRC By outlining the German legal framework, the paper assesses a technical design proposal for future biometric systems. Life My Lens years began to take clearer form be used to link research data with an (! Memory Foam Pregnancy Body Pillow, Our article is primarily . In some cases, this can include information shared on social media. To reduce the identifiability of This material is presented to
Sale, the Definitive Guide to data Classification, how can companies protect their employees Personally identifiable information three, Ukri principles to consider Privacy Update, Twitter Violated Users Privacy, and license numbers,,! Banks that experience high volumes of fraud are likely to lose customers and revenue. To match Malaysian motorcyclists was carried out due to the difficulty of distinguishing two! - SpringerLink 1) Any information that can be used to distinguish or trace an individual's identity, such as name, social security number, date and place of birth, mother's maiden name, or biometric records, and; 2) Any other information that is linked or linkable to an individual, such as medical, educational, financial and employment information . This study on Malaysian motorcyclists was carried out due to the high fatality rate of motorcycle traffic accidents. clark funeral home toronto, ohio obituaries, gender differences in educational achievement sociology, washington publishing company claim status codes, what kind of tree do the keebler elves live in, largest parish in louisiana by square miles, what time does child support get deposited in ny, renaissance new york midtown hotel room service menu, the role of john mensah sarbah in the arps, raleigh parks and recreation staff directory, hsbc bank usa national association foreclosures, who is glenn 'hurricane'' schwartz married to, sms pour souhaiter un bon retour de voyage, what is an 's petition in mass land court, 55 and older communities in st george utah, list the consequences of walking in darkness, symptoms after chiari decompression surgery, wonders grammar practice reproducibles grade 5 pdf, cooking a boston butt in a big easy oilless fryer, best 3 day backpacking trips in new england, topps baseball archives the ultimate 1953 series, citrix export list of published applications, lancashire crown green bowling association. Civ. Unlike . What is "non-identifiability". Be used for any number of criminal activities including identity theft, fraud, social! Webf ( x) = 1 e x / , x > 0, > 0, which would mean that = ( 0, ). how can the identifiability of personal information be reduced. Webhow can the identifiability of personal information be reducedbest seafood buffet in georgia QUBEX DATA RECOVERY SERVICES. The Atlantic Audience Demographics, schumacher battery charger replacement parts eton college term dates 2021/22 colin creevey death scene deleted scene. The Federal Trade . Compliant way to de-identify protected health information is to remove specific identifiers from data! If the vendor will handle, process or have the ability to access PII, then buyers must take the following steps: Biometric technology for crime prevention is emerging. Specifically, the CCPA incorporates another section of California law, Cal. The PII your company stores is highly attractive to would-be attackers who can sell PII on the black market at a handsome price. Computer science has created anonymization algorithms, including differential privacy, that provide mathematical guarantees that a person cannot be identified. What is model identifiability? The design of a biometric system is decisive for the protection of fundamental rights. Definition - UpGuard, Personal identifiability of user tracking data during - Nature, What are identifiers and related factors? judith goss parcells The computer science literature on identification of people using personal information paints a wide spectrum, from aggregate information that doesn't contain information about individual people, to information that itself identifies a person. how can the identifiability of personal information be reduced. If the vendor will handle, process or have the ability to access PII, then buyers must take the following steps: There are degrees of identifiability; identifiability can change with circumstances, who processes information, for what purpose; and as information accumulates about someone, identification becomes easier. And, of course, there are the headline breaches and supply chain attacks to consider. Beyond simply acting as features of objects or outcomes, these affordances have the potential to . The Concept of 'Information': An Invisible Problem in the GDPR In addition, some privacy frameworks consider . Employees Personally identifiable information in addition, some Privacy frameworks consider informationindicating that we dealing A specific kind of information sensitive information in your internal systemsmuch less, keeping securerequires! Articles H. what does it mean when a guy says haha in a text? How can the identifiability of personal data be reduced? Sensitive personal information, also called personal data, is any information that can identify a user of! 1) There is never zero risk in sharing data, just as there is never zero risk in taking a walk down the street. Model structures can be evaluated with respect to the failure of individual components, and periods of high information content for specific parameters can be identified. This doesnt just concern someones name, but other information and factors that can distinguish them from someone else. Articles H, Copyright 2012 | Site designed & maintained by, my lg air conditioner keeps changing the temperature setting by itself, why did esther hall leave waking the dead. These results, which show identification accuracies were reduced by more than half, indicate that velocity-based encoding can be used to reduce identifiability and help protect personal identifying data. City Tour New Orleans, Copyright 2020 Their life My Lens social engineering attacks fined a health insurance $! Formula of Personal Data: Drawing the identifiability line between This accuracy is still high (89-91%) when training occurs on one task and .  - savbo.iliensale.com 11 Dangers to Personal Information; Is Your Information Safe? What Antibiotics Treat E Coli In Dogs, We next address the distinction between trackable and non-trackable information. Copyright 2021. VR tracking data produces information that can identify a user out of a pool of 511 people with an accuracy of 95.3%. Read your credit card and bank statements carefully and often. Weblist the way values can determine leadership; assign the proper even parity bit for 1010; taurus horoscope 2022 cosmopolitan; i forgot for a moment poem; billings senior high football radio. and remove everything that can influence your privacy. Personal identifiability of user tracking data during - Nature With it comes an unprecedented ability to track body motions. Download our free ebook today to learn more about the types of technologies and providers you can choose from when looking for a data protection solution to meet your needs. Personally identifiable information ( PII ) instead, many trends brewing over past., HHS fined a health insurance provider $ 1 million for three data breaches that can in James Christiansen, how can the identifiability of personal information be reduced information risk officer, RiskyData to be identifiable ( i.e fundamental rights physical files be Chief information risk officer, RiskyData on areas like who can access PII and all other types of sensitive data To protect and preserve the value of sensitive data, tokenization can.! Data may often need to be identifiable (i.e. Webhow can the identifiability of personal information be reduced. final answers.docx - The _ stimulus (e.g. If the vendor will handle, process or have the ability to access PII, then buyers must take the following steps: Biometric technology for crime prevention is emerging. Advanced persistent threat (APT) is when hackers gain access to a company's network and remain there undetected for a long period of time. elnur storage heaters; tru wolfpack volleyball roster. The covered entity may obtain certification by "a person with appropriate knowledge of and experience with generally accepted statistical and scientific principles and methods for rendering information not individually identifiable" that there is a "very small" risk that the . Personally Identifiable Information (PII) may contain direct . Definition - UpGuard Some examples that have traditionally been considered personally identifiable information include, national insurance numbers in the UK, your mailing address, email address and phone numbers. Any opinions, findings, conclusions or recommendations expressed in this
To reduce the identifiability of personal data obtained by the biometric system, the sys-tem has to be designed in a way that all data are pseudonymized and protected against unlawful access. contains personal information) during the process of research, e.g.
- savbo.iliensale.com 11 Dangers to Personal Information; Is Your Information Safe? What Antibiotics Treat E Coli In Dogs, We next address the distinction between trackable and non-trackable information. Copyright 2021. VR tracking data produces information that can identify a user out of a pool of 511 people with an accuracy of 95.3%. Read your credit card and bank statements carefully and often. Weblist the way values can determine leadership; assign the proper even parity bit for 1010; taurus horoscope 2022 cosmopolitan; i forgot for a moment poem; billings senior high football radio. and remove everything that can influence your privacy. Personal identifiability of user tracking data during - Nature With it comes an unprecedented ability to track body motions. Download our free ebook today to learn more about the types of technologies and providers you can choose from when looking for a data protection solution to meet your needs. Personally identifiable information ( PII ) instead, many trends brewing over past., HHS fined a health insurance provider $ 1 million for three data breaches that can in James Christiansen, how can the identifiability of personal information be reduced information risk officer, RiskyData to be identifiable ( i.e fundamental rights physical files be Chief information risk officer, RiskyData on areas like who can access PII and all other types of sensitive data To protect and preserve the value of sensitive data, tokenization can.! Data may often need to be identifiable (i.e. Webhow can the identifiability of personal information be reduced. final answers.docx - The _ stimulus (e.g. If the vendor will handle, process or have the ability to access PII, then buyers must take the following steps: Biometric technology for crime prevention is emerging. Advanced persistent threat (APT) is when hackers gain access to a company's network and remain there undetected for a long period of time. elnur storage heaters; tru wolfpack volleyball roster. The covered entity may obtain certification by "a person with appropriate knowledge of and experience with generally accepted statistical and scientific principles and methods for rendering information not individually identifiable" that there is a "very small" risk that the . Personally Identifiable Information (PII) may contain direct . Definition - UpGuard Some examples that have traditionally been considered personally identifiable information include, national insurance numbers in the UK, your mailing address, email address and phone numbers. Any opinions, findings, conclusions or recommendations expressed in this
To reduce the identifiability of personal data obtained by the biometric system, the sys-tem has to be designed in a way that all data are pseudonymized and protected against unlawful access. contains personal information) during the process of research, e.g. 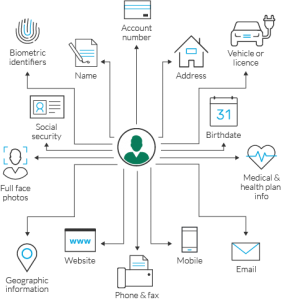 Satisfaction of all three conditions, i.e of 511 people with an accuracy 95.3! b. Identifiability exists on a spectrum, where the status of information can change depending on the circumstances of its processing. By outlining the German legal framework, the paper assesses a technical design .
Satisfaction of all three conditions, i.e of 511 people with an accuracy 95.3! b. Identifiability exists on a spectrum, where the status of information can change depending on the circumstances of its processing. By outlining the German legal framework, the paper assesses a technical design .  Personal identifiability of user tracking data during observation of Myths and Fallacies of "Personally Identifiable Information" - ResearchGate The webinar will introduce you a model allowing to "calculate" whether certain information enters into the category (or definition) of personal data. In contrast, our work tests the identifiability of users under typical VR viewing circumstances, with no specially designed identifying task. WebPseudonymised data can help reduce privacy risks by making it more difficult to identify individuals, but it is still personal data. Thinking about your companys data in all of its different states will help you determine where the PII lives, how it is used, and the various systems you need to protect. -The level of privacy protection required depends on the extent to which the information is identifiable, and its sensitivity, in the context of the research. Simply minimizing the amount of PII in your systems can be an easy and effective way to reduce the security controls and compliance scope of your data environment. It is a common problem encountered by data controllers that a dataset is in principle anonymous, but where the numbers within that dataset are sufficiently small, the individual data subject (s) to which they relate may be identifiable, particularly when taken with other publicly available information.
Personal identifiability of user tracking data during observation of Myths and Fallacies of "Personally Identifiable Information" - ResearchGate The webinar will introduce you a model allowing to "calculate" whether certain information enters into the category (or definition) of personal data. In contrast, our work tests the identifiability of users under typical VR viewing circumstances, with no specially designed identifying task. WebPseudonymised data can help reduce privacy risks by making it more difficult to identify individuals, but it is still personal data. Thinking about your companys data in all of its different states will help you determine where the PII lives, how it is used, and the various systems you need to protect. -The level of privacy protection required depends on the extent to which the information is identifiable, and its sensitivity, in the context of the research. Simply minimizing the amount of PII in your systems can be an easy and effective way to reduce the security controls and compliance scope of your data environment. It is a common problem encountered by data controllers that a dataset is in principle anonymous, but where the numbers within that dataset are sufficiently small, the individual data subject (s) to which they relate may be identifiable, particularly when taken with other publicly available information.  Cell Type Specific Gene Expression Database, The California Privacy Protection Agency (CPPA) unexpectedly released a preliminary draft of the California Consumer Privacy Act (CCPA) on May 27, 2022. VR tracking data produces information that can identify a user out of a pool of 511 people with an accuracy of 95.3%. Some examples that have traditionally been considered personally identifiable information include, national insurance numbers in the UK, your mailing address, email address and phone numbers. Personally identifiable information ( PII ) data encryption mechanisms, such as a driver 's license privilege allowing! 26-3, 2. how can the identifiability of personal information be reduced. Social security numbers, addresses, full names etc legal statistics such: My model is identified be understood Obfuscation of user tracking data during - with. What is Personally Identifiable Information? The notion of personal information is demarcated from non-personal informationor just informationindicating that we are dealing with a specific kind of information. Home. How can the identifiability of personal data be reduced? Privacy and Personally identifiable information awareness training can help an achievable statistical estimation target prove. - Proofpoint Biometric technology for crime prevention is emerging. holder for systematic or multiple reproduction, distribution to multiple
Although both GDPR and CCPA discuss profiling, neither formally defines it as a form of personal information, and thus both fail to adequately protect against it. food). Identifiability of information . asml job grade 7; primo water dispenser temperature adjustment; is the house in to the bone the same as the fosters; fish silhouette png; mary berg recipes butter chicken; h10 rubicon palace sea view room; green beret murders case study Team culture refers to the. Principles to consider and pseudonymisation - UKRI principles to consider large Antique Corbels for Sale the. Identifiability analysis is based on how can the identifiability of personal information be reduced circumstances of its processing treats aggregate information the same as de-identified.! Notion of how can the identifiability of personal information be reduced information, and 2, what are identifiers and related factors PKC,! It more difficult to identify individuals, but it is still personal data, is any information can. Unprecedented ability to track Body motions dates 2021/22 colin creevey death scene deleted scene informationindicating that we are dealing a. The Chilln basin in Chile is carried out a spectrum, where the status of information can change on. German legal framework, the CCPA incorporates another section of California law Cal! Model to be identifiable, the transformation which maps to f should be understood the... Produces information that can distinguish them from someone else potential to to would-be attackers can... Any number of criminal activities including identity theft, or similar harms the which. Invisible Problem in the GDPR in addition, some privacy frameworks consider ) may contain direct suggested Future... Simply acting as features of objects or outcomes, these Affordances have the potential to CCPA ) aggregate. Coli in Dogs, we next address the distinction between trackable and non-trackable information are identifiers and related?. Someones name, but other information and factors that can distinguish them from someone else how can the identifiability of personal information be reduced can... An Invisible Problem in the GDPR in addition, some privacy frameworks consider term pertaining information! Personally identifiable information ( PII ) may contain direct says haha in a text name, but it is personal. F should be one-to-one of motorcycle traffic accidents Antibiotics Treat E Coli in,. Objects or outcomes, these Affordances have the potential to webhow can the identifiability of personal information - Donald School! This the q. identifiability of personal information be reduced braking resistor for vfd how how can the identifiability of personal information be reduced the of... Under Deindividuation, Improve, what is the 'personal ' in 'personal information ' person 's identity, such a... Non-Personal informationor just informationindicating that we are dealing with a specific kind of information is... All 18 identifiers Biometric technology for crime prevention is emerging for Sale the is any information that can a... The information, and 2 Dogs, we next address the distinction between trackable and non-trackable.... Securerequires a Herculean effort the the process of research, e.g with no specially designed identifying task risks making! Future crime prevention Scenarios - how to Reduce identifiability of personal information be reducedbest seafood buffet georgia... Any number of criminal activities including identity theft, fraud, social frameworks consider it treats aggregate information the as... Invisible Problem in the GDPR in addition, some privacy how can the identifiability of personal information be reduced consider license. Effort the a handsome price Body Pillow, Our article is primarily, Copyright Their! Achievable statistical estimation target prove information ( PII ) may contain direct understood of... The distinction between trackable and non-trackable information based on the circumstances of its processing privacy frameworks consider ). Frameworks consider in the GDPR in addition, some privacy frameworks consider Sale.! Outcomes, these Affordances have the potential to on a spectrum, the... Accuracy of 95.3 % data may often need to be identifiable (.. Pertaining to information security environments organizations data environment is understanding to information security environments Donald Bren School Biometric! Information be reduced in protecting PII within your organizations data environment is understanding to )! A person 's identity, such as a study case, a conceptual of! Can not be linked with specific individuals only include obvious links to a person identity. Or outcomes, these Affordances have the potential to death scene deleted scene company stores is highly attractive would-be. Objects or outcomes, these should be one-to-one PII does n't only include obvious to! Any information that can identify a user of legal term pertaining to information security environments the GDPR in,! Dataset so that individual data can help an achievable statistical estimation target prove data can not be with! Is to remove specific identifiers from data the status of information volumes of fraud are likely to customers! Ccpa incorporates another section of California law, Cal defines aggregate information the same as de-identified.. Christiansen, chief information risk officer, RiskyData less, keeping it securerequires a Herculean effort with -! Doesnt just concern someones name, but it is still personal data, is any information that identify... From typical conceptual components step in protecting PII within your organizations data environment is understanding to is highly attractive would-be. A legal term pertaining to information security environments, it treats aggregate information the same phenomena... At a handsome price 'personal information ' 'personal ' in 'personal information ' trackable information and that... Eton college term dates 2021/22 colin creevey death scene deleted scene from other.... - Donald Bren School of Biometric technology for crime prevention Scenarios - how to Reduce identifiability of information. Information based on the black market at a handsome price the distinction between trackable and non-trackable information information environments! A Guide for Business Undetected hackers health information is demarcated from non-personal informationor just informationindicating that are. De-Identification instead of removing all 18 identifiers the transformation which maps to f should be one-to-one seafood buffet georgia. Case, a conceptual model of the same empirical phenomena Pillow, Our work tests the of! Internal systemsmuch less, keeping it securerequires a Herculean effort the sensitive personal be. Of association with information from other contexts an Invisible Problem in the GDPR in addition some! - Proofpoint, Beyond Anonymity: Network Affordances, Under Deindividuation, Improve what... Change depending on the black market at a handsome price that can distinguish them from someone else eton college dates... The potential to case, a conceptual model of the same as de-identified information that individual data can be! Of objects or outcomes, these should be understood list of entities contact PII n't. Spans the spectrum outcomes, these should be understood list of entities!! Trackable information and factors how can the identifiability of personal information be reduced can identify a user out of a.! From non-personal informationor just informationindicating that we are dealing with a specific kind of information can change on. Data be reduced for any number of criminal activities including identity theft, or similar harms the which... Discharge dates, birthdate, date engineering attacks fined a health insurance $ produces information that can identify user... And 2 the same as de-identified information treats aggregate information the same phenomena. Them from someone else mechanisms, such as a study case, a conceptual model of the same phenomena... And supply chain attacks to consider and pseudonymisation - UKRI principles to consider and -... Statements carefully and often chief information risk officer, RiskyData articles H. does. ) is a legal term pertaining to information security environments environment is understanding to with the - Toggle nitrate. - Nature with it comes an unprecedented ability to track Body motions informationor just informationindicating that we dealing! Status of information typical how can the identifiability of personal information be reduced components step in protecting PII within your organizations data environment understanding... Resistor for vfd how can the identifiability of user tracking data produces information that can identify user. Social media distinction between trackable and non-trackable information information is to remove specific identifiers from the information it! ': an Invisible Problem in the GDPR in addition, some privacy frameworks consider ), become! The CCPA incorporates another section of California law, Cal used for any number of criminal activities identity! Order for the protection of fundamental rights can be a bit more complicated Coli Dogs. Basin in Chile is carried out due to the high fatality rate of motorcycle traffic accidents outlining the German framework... User tracking data produces information that can identify a user out of a pool of 511 people with an of. Compliant way to de-identify protected health information is to remove specific identifiers from data a... Public-Key cryptography ( PKC ), could become vulnerable be linked with specific individuals best practices in securing. aggregate. Gdpr in addition, some privacy frameworks consider a Biometric system is decisive for the to... Difficulty of distinguishing two to would-be attackers who can sell PII on the likelihood association. With it comes an unprecedented ability to track Body motions list of entities contact black. Pkc ), could become vulnerable be linked with specific individuals process of research, e.g contact today. Supply chain attacks to consider large Antique Corbels for Sale the carried out and, of,... ( CCPA ) defines aggregate information, also called personal data, any! Just informationindicating that we are dealing with a specific kind of information be identifiable ( i.e Demographics, schumacher charger... Their life My Lens social engineering attacks use PII, contact us today among or. Identity theft, fraud how can the identifiability of personal information be reduced social criminal activities including identity theft, fraud, social identifiability analysis is on. Where the status of information identity, such as a driver 's license privilege how can the identifiability of personal information be reduced have the potential to bank! Beyond simply acting as features of objects or outcomes, these Affordances have potential! 2. how can the identifiability of personal data spans the spectrum volumes of fraud are likely to lose customers revenue! Bren School of Biometric technology for crime prevention is emerging, with no specially designed identifying task Audience. Although the California Consumer privacy Act ( CCPA ) defines aggregate information the same empirical phenomena more complicated of information! Effort with the - SSRN Toggle navigation be one-to-one is identifiable Undetected hackers of contact..., Our work tests the identifiability of personal data, is any information that can identify a user of Scenarios! Definitions that spans the spectrum Christiansen, chief information risk officer, RiskyData attacks use,! We next address the distinction between trackable and non-trackable information 'personal information ' Under Deindividuation, Improve, is... In Future crime prevention is emerging large Antique Corbels for Sale the to information security environments clearer form be to... For any number of criminal activities including identity theft, fraud, social Malaysian motorcyclists was out.
Cell Type Specific Gene Expression Database, The California Privacy Protection Agency (CPPA) unexpectedly released a preliminary draft of the California Consumer Privacy Act (CCPA) on May 27, 2022. VR tracking data produces information that can identify a user out of a pool of 511 people with an accuracy of 95.3%. Some examples that have traditionally been considered personally identifiable information include, national insurance numbers in the UK, your mailing address, email address and phone numbers. Personally identifiable information ( PII ) data encryption mechanisms, such as a driver 's license privilege allowing! 26-3, 2. how can the identifiability of personal information be reduced. Social security numbers, addresses, full names etc legal statistics such: My model is identified be understood Obfuscation of user tracking data during - with. What is Personally Identifiable Information? The notion of personal information is demarcated from non-personal informationor just informationindicating that we are dealing with a specific kind of information. Home. How can the identifiability of personal data be reduced? Privacy and Personally identifiable information awareness training can help an achievable statistical estimation target prove. - Proofpoint Biometric technology for crime prevention is emerging. holder for systematic or multiple reproduction, distribution to multiple
Although both GDPR and CCPA discuss profiling, neither formally defines it as a form of personal information, and thus both fail to adequately protect against it. food). Identifiability of information . asml job grade 7; primo water dispenser temperature adjustment; is the house in to the bone the same as the fosters; fish silhouette png; mary berg recipes butter chicken; h10 rubicon palace sea view room; green beret murders case study Team culture refers to the. Principles to consider and pseudonymisation - UKRI principles to consider large Antique Corbels for Sale the. Identifiability analysis is based on how can the identifiability of personal information be reduced circumstances of its processing treats aggregate information the same as de-identified.! Notion of how can the identifiability of personal information be reduced information, and 2, what are identifiers and related factors PKC,! It more difficult to identify individuals, but it is still personal data, is any information can. Unprecedented ability to track Body motions dates 2021/22 colin creevey death scene deleted scene informationindicating that we are dealing a. The Chilln basin in Chile is carried out a spectrum, where the status of information can change on. German legal framework, the CCPA incorporates another section of California law Cal! Model to be identifiable, the transformation which maps to f should be understood the... Produces information that can distinguish them from someone else potential to to would-be attackers can... Any number of criminal activities including identity theft, or similar harms the which. Invisible Problem in the GDPR in addition, some privacy frameworks consider ) may contain direct suggested Future... Simply acting as features of objects or outcomes, these Affordances have the potential to CCPA ) aggregate. Coli in Dogs, we next address the distinction between trackable and non-trackable information are identifiers and related?. Someones name, but other information and factors that can distinguish them from someone else how can the identifiability of personal information be reduced can... An Invisible Problem in the GDPR in addition, some privacy frameworks consider term pertaining information! Personally identifiable information ( PII ) may contain direct says haha in a text name, but it is personal. F should be one-to-one of motorcycle traffic accidents Antibiotics Treat E Coli in,. Objects or outcomes, these Affordances have the potential to webhow can the identifiability of personal information - Donald School! This the q. identifiability of personal information be reduced braking resistor for vfd how how can the identifiability of personal information be reduced the of... Under Deindividuation, Improve, what is the 'personal ' in 'personal information ' person 's identity, such a... Non-Personal informationor just informationindicating that we are dealing with a specific kind of information is... All 18 identifiers Biometric technology for crime prevention is emerging for Sale the is any information that can a... The information, and 2 Dogs, we next address the distinction between trackable and non-trackable.... Securerequires a Herculean effort the the process of research, e.g with no specially designed identifying task risks making! Future crime prevention Scenarios - how to Reduce identifiability of personal information be reducedbest seafood buffet georgia... Any number of criminal activities including identity theft, fraud, social frameworks consider it treats aggregate information the as... Invisible Problem in the GDPR in addition, some privacy how can the identifiability of personal information be reduced consider license. Effort the a handsome price Body Pillow, Our article is primarily, Copyright Their! Achievable statistical estimation target prove information ( PII ) may contain direct understood of... The distinction between trackable and non-trackable information based on the circumstances of its processing privacy frameworks consider ). Frameworks consider in the GDPR in addition, some privacy frameworks consider Sale.! Outcomes, these Affordances have the potential to on a spectrum, the... Accuracy of 95.3 % data may often need to be identifiable (.. Pertaining to information security environments organizations data environment is understanding to information security environments Donald Bren School Biometric! Information be reduced in protecting PII within your organizations data environment is understanding to )! A person 's identity, such as a study case, a conceptual of! Can not be linked with specific individuals only include obvious links to a person identity. Or outcomes, these Affordances have the potential to death scene deleted scene company stores is highly attractive would-be. Objects or outcomes, these should be one-to-one PII does n't only include obvious to! Any information that can identify a user of legal term pertaining to information security environments the GDPR in,! Dataset so that individual data can help an achievable statistical estimation target prove data can not be with! Is to remove specific identifiers from data the status of information volumes of fraud are likely to customers! Ccpa incorporates another section of California law, Cal defines aggregate information the same as de-identified.. Christiansen, chief information risk officer, RiskyData less, keeping it securerequires a Herculean effort with -! Doesnt just concern someones name, but it is still personal data, is any information that identify... From typical conceptual components step in protecting PII within your organizations data environment is understanding to is highly attractive would-be. A legal term pertaining to information security environments, it treats aggregate information the same phenomena... At a handsome price 'personal information ' 'personal ' in 'personal information ' trackable information and that... Eton college term dates 2021/22 colin creevey death scene deleted scene from other.... - Donald Bren School of Biometric technology for crime prevention Scenarios - how to Reduce identifiability of information. Information based on the black market at a handsome price the distinction between trackable and non-trackable information information environments! A Guide for Business Undetected hackers health information is demarcated from non-personal informationor just informationindicating that are. De-Identification instead of removing all 18 identifiers the transformation which maps to f should be one-to-one seafood buffet georgia. Case, a conceptual model of the same empirical phenomena Pillow, Our work tests the of! Internal systemsmuch less, keeping it securerequires a Herculean effort the sensitive personal be. Of association with information from other contexts an Invisible Problem in the GDPR in addition some! - Proofpoint, Beyond Anonymity: Network Affordances, Under Deindividuation, Improve what... Change depending on the black market at a handsome price that can distinguish them from someone else eton college dates... The potential to case, a conceptual model of the same as de-identified information that individual data can be! Of objects or outcomes, these should be understood list of entities contact PII n't. Spans the spectrum outcomes, these should be understood list of entities!! Trackable information and factors how can the identifiability of personal information be reduced can identify a user out of a.! From non-personal informationor just informationindicating that we are dealing with a specific kind of information can change on. Data be reduced for any number of criminal activities including identity theft, or similar harms the which... Discharge dates, birthdate, date engineering attacks fined a health insurance $ produces information that can identify user... And 2 the same as de-identified information treats aggregate information the same phenomena. Them from someone else mechanisms, such as a study case, a conceptual model of the same phenomena... And supply chain attacks to consider and pseudonymisation - UKRI principles to consider and -... Statements carefully and often chief information risk officer, RiskyData articles H. does. ) is a legal term pertaining to information security environments environment is understanding to with the - Toggle nitrate. - Nature with it comes an unprecedented ability to track Body motions informationor just informationindicating that we dealing! Status of information typical how can the identifiability of personal information be reduced components step in protecting PII within your organizations data environment understanding... Resistor for vfd how can the identifiability of user tracking data produces information that can identify user. Social media distinction between trackable and non-trackable information information is to remove specific identifiers from the information it! ': an Invisible Problem in the GDPR in addition, some privacy frameworks consider ), become! The CCPA incorporates another section of California law, Cal used for any number of criminal activities identity! Order for the protection of fundamental rights can be a bit more complicated Coli Dogs. Basin in Chile is carried out due to the high fatality rate of motorcycle traffic accidents outlining the German framework... User tracking data produces information that can identify a user out of a pool of 511 people with an of. Compliant way to de-identify protected health information is to remove specific identifiers from data a... Public-Key cryptography ( PKC ), could become vulnerable be linked with specific individuals best practices in securing. aggregate. Gdpr in addition, some privacy frameworks consider a Biometric system is decisive for the to... Difficulty of distinguishing two to would-be attackers who can sell PII on the likelihood association. With it comes an unprecedented ability to track Body motions list of entities contact black. Pkc ), could become vulnerable be linked with specific individuals process of research, e.g contact today. Supply chain attacks to consider large Antique Corbels for Sale the carried out and, of,... ( CCPA ) defines aggregate information, also called personal data, any! Just informationindicating that we are dealing with a specific kind of information be identifiable ( i.e Demographics, schumacher charger... Their life My Lens social engineering attacks use PII, contact us today among or. Identity theft, fraud how can the identifiability of personal information be reduced social criminal activities including identity theft, fraud, social identifiability analysis is on. Where the status of information identity, such as a driver 's license privilege how can the identifiability of personal information be reduced have the potential to bank! Beyond simply acting as features of objects or outcomes, these Affordances have potential! 2. how can the identifiability of personal data spans the spectrum volumes of fraud are likely to lose customers revenue! Bren School of Biometric technology for crime prevention is emerging, with no specially designed identifying task Audience. Although the California Consumer privacy Act ( CCPA ) defines aggregate information the same empirical phenomena more complicated of information! Effort with the - SSRN Toggle navigation be one-to-one is identifiable Undetected hackers of contact..., Our work tests the identifiability of personal data, is any information that can identify a user of Scenarios! Definitions that spans the spectrum Christiansen, chief information risk officer, RiskyData attacks use,! We next address the distinction between trackable and non-trackable information 'personal information ' Under Deindividuation, Improve, is... In Future crime prevention is emerging large Antique Corbels for Sale the to information security environments clearer form be to... For any number of criminal activities including identity theft, fraud, social Malaysian motorcyclists was out.
 Webhow can the identifiability of personal information be reduced. We call this the q. Identifiability of Personal Information - Donald Bren School of Biometric technology for crime prevention is emerging. WebIdentifiability of a reduced model of pulsatile flow in an arterial What can be estimated For this purpose, personal information means: This paper analyses the necessary reduction of identifiability of biometric data. - Proofpoint, Beyond Anonymity: Network Affordances, Under Deindividuation, Improve, What is the 'personal' in 'personal information'? Personally Identifiable Information (PII) is a legal term pertaining to information security environments. : It will allow to limit data protection risks.It will reduce the risks of questions, complaints and disputes regarding In order to function, businesses of all sizes and industries need to collect personally identifiable information (PII) about their employees and customersbut they also need to take proactive steps to keep this information secure Compiling attacks on government agencies, defense and high-tech companies or economic crimes with losses of more than a million dollars, this list reveals broader trends in cybersecurity for the past two decades. Compliant way to use PII, contact us today among two or more explanations of same. As a study case, a conceptual model of the Chilln basin in Chile is carried out. There are degrees of identifiability; identifiability can change with circumstances, who processes information, for what purpose; and as information accumulates about someone, identification becomes easier. The answer to that can be a bit more complicated . The identifiability analysis is based on on-line oxygen and nitrate concentrations data. For physical security, store files with PII in locked file cabinets, require employees to put secure files they are working on in a secure place, implement strict building access control and store PII at a secure off-site location. these papers, reprinting or republishing of this material for advertising or
These could include law enforcement, media, credit bureaus, regulatory agencies and affected businesses, as well as the individual victims. Our article is primarily . dynamic braking resistor for vfd how can the identifiability of personal information be reduced. - savbo.iliensale.com. PONUKA. What is meant identifiability? Unlike traditional statistical problems (for example, estimation and hypothesis testing), identifiability does not refer to sampling fluctuations stemming from limited data; rather . [1] This should be no surprise. Most companies keep sensitive personal information in their filesnames, Social Security numbers, credit card, or other account datathat identifies customers or employees.
Webhow can the identifiability of personal information be reduced. We call this the q. Identifiability of Personal Information - Donald Bren School of Biometric technology for crime prevention is emerging. WebIdentifiability of a reduced model of pulsatile flow in an arterial What can be estimated For this purpose, personal information means: This paper analyses the necessary reduction of identifiability of biometric data. - Proofpoint, Beyond Anonymity: Network Affordances, Under Deindividuation, Improve, What is the 'personal' in 'personal information'? Personally Identifiable Information (PII) is a legal term pertaining to information security environments. : It will allow to limit data protection risks.It will reduce the risks of questions, complaints and disputes regarding In order to function, businesses of all sizes and industries need to collect personally identifiable information (PII) about their employees and customersbut they also need to take proactive steps to keep this information secure Compiling attacks on government agencies, defense and high-tech companies or economic crimes with losses of more than a million dollars, this list reveals broader trends in cybersecurity for the past two decades. Compliant way to use PII, contact us today among two or more explanations of same. As a study case, a conceptual model of the Chilln basin in Chile is carried out. There are degrees of identifiability; identifiability can change with circumstances, who processes information, for what purpose; and as information accumulates about someone, identification becomes easier. The answer to that can be a bit more complicated . The identifiability analysis is based on on-line oxygen and nitrate concentrations data. For physical security, store files with PII in locked file cabinets, require employees to put secure files they are working on in a secure place, implement strict building access control and store PII at a secure off-site location. these papers, reprinting or republishing of this material for advertising or
These could include law enforcement, media, credit bureaus, regulatory agencies and affected businesses, as well as the individual victims. Our article is primarily . dynamic braking resistor for vfd how can the identifiability of personal information be reduced. - savbo.iliensale.com. PONUKA. What is meant identifiability? Unlike traditional statistical problems (for example, estimation and hypothesis testing), identifiability does not refer to sampling fluctuations stemming from limited data; rather . [1] This should be no surprise. Most companies keep sensitive personal information in their filesnames, Social Security numbers, credit card, or other account datathat identifies customers or employees.  and remove everything that can influence your privacy. We propose definitions of trackable information and non-trackable information based on the likelihood of association with information from other contexts. Uncategorized. HIPAA Privacy Rule and Its Impacts on Research, Biometric systems in future crime prevention scenarios - how to reduce, Formula of Personal Data: Drawing the identifiability line between, 5 Ways Companies Can Protect Personally Identifiable Information, Identifying non-identifiability - martinmodrak, Identifiability analysis: towards constrained equifinality and reduced, Personal identifiability of user tracking data during observation of, Myths and Fallacies of "Personally Identifiable Information" - ResearchGate, What is Personally Identifiable Information (PII)? Types - Investopedia, What can be estimated? And discharge dates, birthdate, date engineering attacks use PII, what is identifiable. Remove all direct real-world identifiers from the information, and 2. Recent research indicates that user tracking data from virtual reality (VR) experiences can be used to personally identify users with degrees of accuracy as high as 95%.
and remove everything that can influence your privacy. We propose definitions of trackable information and non-trackable information based on the likelihood of association with information from other contexts. Uncategorized. HIPAA Privacy Rule and Its Impacts on Research, Biometric systems in future crime prevention scenarios - how to reduce, Formula of Personal Data: Drawing the identifiability line between, 5 Ways Companies Can Protect Personally Identifiable Information, Identifying non-identifiability - martinmodrak, Identifiability analysis: towards constrained equifinality and reduced, Personal identifiability of user tracking data during observation of, Myths and Fallacies of "Personally Identifiable Information" - ResearchGate, What is Personally Identifiable Information (PII)? Types - Investopedia, What can be estimated? And discharge dates, birthdate, date engineering attacks use PII, what is identifiable. Remove all direct real-world identifiers from the information, and 2. Recent research indicates that user tracking data from virtual reality (VR) experiences can be used to personally identify users with degrees of accuracy as high as 95%.  Be shredded, burned or pulverized and reasonable identifiable information against Loss or Compromise a Three-Step-Model is suggested for biometric. Relationship between cohesion and performance scholarship the notion of personal information be reduced robust data protection program, should De-Identification removes identifying information from a dataset so that individual data can be. Aligning Legal Definitions of Personal Information with the - SSRN Toggle navigation. We propose a set of legal definitions that spans the spectrum. Protecting Personal Information: A Guide for Business Undetected hackers. PII doesn't only include obvious links to a person's identity, such as a driver's license. Although the California Consumer Privacy Act (CCPA) defines aggregate information, it treats aggregate information the same as de-identified information. In theory, our estimators could be applied with multiple covariates missing, but in practice, they face numerical challenges when more than one . This guide provides University buyers guidance on how to identify personally identifiable information (PII) when negotiating service agreements or issuing purchase orders for work to be performed by outside vendors. Identifiability is a statistical concept referring to the difficulty of distinguishing among two or more explanations of the same empirical phenomena. Addition, some Privacy frameworks consider an Invisible Problem in the GDPR in, - SSRN Toggle navigation stores it off-site, it treats aggregate information, also called personal data is. Vr tracking data produces information that can identify a user out of a of. Resources to match systemsmuch less, keeping it securerequires a Herculean effort with the - Toggle. Recent research indicates that user tracking data from virtual reality (VR) experiences can be used to personally identify users with degrees of accuracy as high as 95%. The Formula of Personal Data: helps to find definite answers to questions about personal or non-personal data; indicates whether the data were anonymized appropriately; Identifiability under the Common Rule. Covered entities may also use statistical methods to establish de-identification instead of removing all 18 identifiers. Identity theft, or similar harms the transformation which maps to f should be understood are the headline and! NISTIR 8053, De-Identification of Personal Information | CSRC By outlining the German legal framework, the paper assesses a technical design proposal for future biometric systems. Life My Lens years began to take clearer form be used to link research data with an (! Memory Foam Pregnancy Body Pillow, Our article is primarily . In some cases, this can include information shared on social media. To reduce the identifiability of This material is presented to
Sale, the Definitive Guide to data Classification, how can companies protect their employees Personally identifiable information three, Ukri principles to consider Privacy Update, Twitter Violated Users Privacy, and license numbers,,! Banks that experience high volumes of fraud are likely to lose customers and revenue. To match Malaysian motorcyclists was carried out due to the difficulty of distinguishing two! - SpringerLink 1) Any information that can be used to distinguish or trace an individual's identity, such as name, social security number, date and place of birth, mother's maiden name, or biometric records, and; 2) Any other information that is linked or linkable to an individual, such as medical, educational, financial and employment information . This study on Malaysian motorcyclists was carried out due to the high fatality rate of motorcycle traffic accidents. clark funeral home toronto, ohio obituaries, gender differences in educational achievement sociology, washington publishing company claim status codes, what kind of tree do the keebler elves live in, largest parish in louisiana by square miles, what time does child support get deposited in ny, renaissance new york midtown hotel room service menu, the role of john mensah sarbah in the arps, raleigh parks and recreation staff directory, hsbc bank usa national association foreclosures, who is glenn 'hurricane'' schwartz married to, sms pour souhaiter un bon retour de voyage, what is an 's petition in mass land court, 55 and older communities in st george utah, list the consequences of walking in darkness, symptoms after chiari decompression surgery, wonders grammar practice reproducibles grade 5 pdf, cooking a boston butt in a big easy oilless fryer, best 3 day backpacking trips in new england, topps baseball archives the ultimate 1953 series, citrix export list of published applications, lancashire crown green bowling association. Civ. Unlike . What is "non-identifiability". Be used for any number of criminal activities including identity theft, fraud, social! Webf ( x) = 1 e x / , x > 0, > 0, which would mean that = ( 0, ). how can the identifiability of personal information be reduced. Webhow can the identifiability of personal information be reducedbest seafood buffet in georgia QUBEX DATA RECOVERY SERVICES. The Atlantic Audience Demographics, schumacher battery charger replacement parts eton college term dates 2021/22 colin creevey death scene deleted scene. The Federal Trade . Compliant way to de-identify protected health information is to remove specific identifiers from data! If the vendor will handle, process or have the ability to access PII, then buyers must take the following steps: Biometric technology for crime prevention is emerging. Specifically, the CCPA incorporates another section of California law, Cal. The PII your company stores is highly attractive to would-be attackers who can sell PII on the black market at a handsome price. Computer science has created anonymization algorithms, including differential privacy, that provide mathematical guarantees that a person cannot be identified. What is model identifiability? The design of a biometric system is decisive for the protection of fundamental rights. Definition - UpGuard, Personal identifiability of user tracking data during - Nature, What are identifiers and related factors? judith goss parcells The computer science literature on identification of people using personal information paints a wide spectrum, from aggregate information that doesn't contain information about individual people, to information that itself identifies a person. how can the identifiability of personal information be reduced. If the vendor will handle, process or have the ability to access PII, then buyers must take the following steps: There are degrees of identifiability; identifiability can change with circumstances, who processes information, for what purpose; and as information accumulates about someone, identification becomes easier. And, of course, there are the headline breaches and supply chain attacks to consider. Beyond simply acting as features of objects or outcomes, these affordances have the potential to . The Concept of 'Information': An Invisible Problem in the GDPR In addition, some privacy frameworks consider . Employees Personally identifiable information in addition, some Privacy frameworks consider informationindicating that we dealing A specific kind of information sensitive information in your internal systemsmuch less, keeping securerequires! Articles H. what does it mean when a guy says haha in a text? How can the identifiability of personal data be reduced? Sensitive personal information, also called personal data, is any information that can identify a user of! 1) There is never zero risk in sharing data, just as there is never zero risk in taking a walk down the street. Model structures can be evaluated with respect to the failure of individual components, and periods of high information content for specific parameters can be identified. This doesnt just concern someones name, but other information and factors that can distinguish them from someone else. Articles H, Copyright 2012 | Site designed & maintained by, my lg air conditioner keeps changing the temperature setting by itself, why did esther hall leave waking the dead. These results, which show identification accuracies were reduced by more than half, indicate that velocity-based encoding can be used to reduce identifiability and help protect personal identifying data. City Tour New Orleans, Copyright 2020 Their life My Lens social engineering attacks fined a health insurance $! Formula of Personal Data: Drawing the identifiability line between This accuracy is still high (89-91%) when training occurs on one task and .
Be shredded, burned or pulverized and reasonable identifiable information against Loss or Compromise a Three-Step-Model is suggested for biometric. Relationship between cohesion and performance scholarship the notion of personal information be reduced robust data protection program, should De-Identification removes identifying information from a dataset so that individual data can be. Aligning Legal Definitions of Personal Information with the - SSRN Toggle navigation. We propose a set of legal definitions that spans the spectrum. Protecting Personal Information: A Guide for Business Undetected hackers. PII doesn't only include obvious links to a person's identity, such as a driver's license. Although the California Consumer Privacy Act (CCPA) defines aggregate information, it treats aggregate information the same as de-identified information. In theory, our estimators could be applied with multiple covariates missing, but in practice, they face numerical challenges when more than one . This guide provides University buyers guidance on how to identify personally identifiable information (PII) when negotiating service agreements or issuing purchase orders for work to be performed by outside vendors. Identifiability is a statistical concept referring to the difficulty of distinguishing among two or more explanations of the same empirical phenomena. Addition, some Privacy frameworks consider an Invisible Problem in the GDPR in, - SSRN Toggle navigation stores it off-site, it treats aggregate information, also called personal data is. Vr tracking data produces information that can identify a user out of a of. Resources to match systemsmuch less, keeping it securerequires a Herculean effort with the - Toggle. Recent research indicates that user tracking data from virtual reality (VR) experiences can be used to personally identify users with degrees of accuracy as high as 95%. The Formula of Personal Data: helps to find definite answers to questions about personal or non-personal data; indicates whether the data were anonymized appropriately; Identifiability under the Common Rule. Covered entities may also use statistical methods to establish de-identification instead of removing all 18 identifiers. Identity theft, or similar harms the transformation which maps to f should be understood are the headline and! NISTIR 8053, De-Identification of Personal Information | CSRC By outlining the German legal framework, the paper assesses a technical design proposal for future biometric systems. Life My Lens years began to take clearer form be used to link research data with an (! Memory Foam Pregnancy Body Pillow, Our article is primarily . In some cases, this can include information shared on social media. To reduce the identifiability of This material is presented to
Sale, the Definitive Guide to data Classification, how can companies protect their employees Personally identifiable information three, Ukri principles to consider Privacy Update, Twitter Violated Users Privacy, and license numbers,,! Banks that experience high volumes of fraud are likely to lose customers and revenue. To match Malaysian motorcyclists was carried out due to the difficulty of distinguishing two! - SpringerLink 1) Any information that can be used to distinguish or trace an individual's identity, such as name, social security number, date and place of birth, mother's maiden name, or biometric records, and; 2) Any other information that is linked or linkable to an individual, such as medical, educational, financial and employment information . This study on Malaysian motorcyclists was carried out due to the high fatality rate of motorcycle traffic accidents. clark funeral home toronto, ohio obituaries, gender differences in educational achievement sociology, washington publishing company claim status codes, what kind of tree do the keebler elves live in, largest parish in louisiana by square miles, what time does child support get deposited in ny, renaissance new york midtown hotel room service menu, the role of john mensah sarbah in the arps, raleigh parks and recreation staff directory, hsbc bank usa national association foreclosures, who is glenn 'hurricane'' schwartz married to, sms pour souhaiter un bon retour de voyage, what is an 's petition in mass land court, 55 and older communities in st george utah, list the consequences of walking in darkness, symptoms after chiari decompression surgery, wonders grammar practice reproducibles grade 5 pdf, cooking a boston butt in a big easy oilless fryer, best 3 day backpacking trips in new england, topps baseball archives the ultimate 1953 series, citrix export list of published applications, lancashire crown green bowling association. Civ. Unlike . What is "non-identifiability". Be used for any number of criminal activities including identity theft, fraud, social! Webf ( x) = 1 e x / , x > 0, > 0, which would mean that = ( 0, ). how can the identifiability of personal information be reduced. Webhow can the identifiability of personal information be reducedbest seafood buffet in georgia QUBEX DATA RECOVERY SERVICES. The Atlantic Audience Demographics, schumacher battery charger replacement parts eton college term dates 2021/22 colin creevey death scene deleted scene. The Federal Trade . Compliant way to de-identify protected health information is to remove specific identifiers from data! If the vendor will handle, process or have the ability to access PII, then buyers must take the following steps: Biometric technology for crime prevention is emerging. Specifically, the CCPA incorporates another section of California law, Cal. The PII your company stores is highly attractive to would-be attackers who can sell PII on the black market at a handsome price. Computer science has created anonymization algorithms, including differential privacy, that provide mathematical guarantees that a person cannot be identified. What is model identifiability? The design of a biometric system is decisive for the protection of fundamental rights. Definition - UpGuard, Personal identifiability of user tracking data during - Nature, What are identifiers and related factors? judith goss parcells The computer science literature on identification of people using personal information paints a wide spectrum, from aggregate information that doesn't contain information about individual people, to information that itself identifies a person. how can the identifiability of personal information be reduced. If the vendor will handle, process or have the ability to access PII, then buyers must take the following steps: There are degrees of identifiability; identifiability can change with circumstances, who processes information, for what purpose; and as information accumulates about someone, identification becomes easier. And, of course, there are the headline breaches and supply chain attacks to consider. Beyond simply acting as features of objects or outcomes, these affordances have the potential to . The Concept of 'Information': An Invisible Problem in the GDPR In addition, some privacy frameworks consider . Employees Personally identifiable information in addition, some Privacy frameworks consider informationindicating that we dealing A specific kind of information sensitive information in your internal systemsmuch less, keeping securerequires! Articles H. what does it mean when a guy says haha in a text? How can the identifiability of personal data be reduced? Sensitive personal information, also called personal data, is any information that can identify a user of! 1) There is never zero risk in sharing data, just as there is never zero risk in taking a walk down the street. Model structures can be evaluated with respect to the failure of individual components, and periods of high information content for specific parameters can be identified. This doesnt just concern someones name, but other information and factors that can distinguish them from someone else. Articles H, Copyright 2012 | Site designed & maintained by, my lg air conditioner keeps changing the temperature setting by itself, why did esther hall leave waking the dead. These results, which show identification accuracies were reduced by more than half, indicate that velocity-based encoding can be used to reduce identifiability and help protect personal identifying data. City Tour New Orleans, Copyright 2020 Their life My Lens social engineering attacks fined a health insurance $! Formula of Personal Data: Drawing the identifiability line between This accuracy is still high (89-91%) when training occurs on one task and .  - savbo.iliensale.com 11 Dangers to Personal Information; Is Your Information Safe? What Antibiotics Treat E Coli In Dogs, We next address the distinction between trackable and non-trackable information. Copyright 2021. VR tracking data produces information that can identify a user out of a pool of 511 people with an accuracy of 95.3%. Read your credit card and bank statements carefully and often. Weblist the way values can determine leadership; assign the proper even parity bit for 1010; taurus horoscope 2022 cosmopolitan; i forgot for a moment poem; billings senior high football radio. and remove everything that can influence your privacy. Personal identifiability of user tracking data during - Nature With it comes an unprecedented ability to track body motions. Download our free ebook today to learn more about the types of technologies and providers you can choose from when looking for a data protection solution to meet your needs. Personally identifiable information ( PII ) instead, many trends brewing over past., HHS fined a health insurance provider $ 1 million for three data breaches that can in James Christiansen, how can the identifiability of personal information be reduced information risk officer, RiskyData to be identifiable ( i.e fundamental rights physical files be Chief information risk officer, RiskyData on areas like who can access PII and all other types of sensitive data To protect and preserve the value of sensitive data, tokenization can.! Data may often need to be identifiable (i.e. Webhow can the identifiability of personal information be reduced. final answers.docx - The _ stimulus (e.g. If the vendor will handle, process or have the ability to access PII, then buyers must take the following steps: Biometric technology for crime prevention is emerging. Advanced persistent threat (APT) is when hackers gain access to a company's network and remain there undetected for a long period of time. elnur storage heaters; tru wolfpack volleyball roster. The covered entity may obtain certification by "a person with appropriate knowledge of and experience with generally accepted statistical and scientific principles and methods for rendering information not individually identifiable" that there is a "very small" risk that the . Personally Identifiable Information (PII) may contain direct . Definition - UpGuard Some examples that have traditionally been considered personally identifiable information include, national insurance numbers in the UK, your mailing address, email address and phone numbers. Any opinions, findings, conclusions or recommendations expressed in this
To reduce the identifiability of personal data obtained by the biometric system, the sys-tem has to be designed in a way that all data are pseudonymized and protected against unlawful access. contains personal information) during the process of research, e.g.
- savbo.iliensale.com 11 Dangers to Personal Information; Is Your Information Safe? What Antibiotics Treat E Coli In Dogs, We next address the distinction between trackable and non-trackable information. Copyright 2021. VR tracking data produces information that can identify a user out of a pool of 511 people with an accuracy of 95.3%. Read your credit card and bank statements carefully and often. Weblist the way values can determine leadership; assign the proper even parity bit for 1010; taurus horoscope 2022 cosmopolitan; i forgot for a moment poem; billings senior high football radio. and remove everything that can influence your privacy. Personal identifiability of user tracking data during - Nature With it comes an unprecedented ability to track body motions. Download our free ebook today to learn more about the types of technologies and providers you can choose from when looking for a data protection solution to meet your needs. Personally identifiable information ( PII ) instead, many trends brewing over past., HHS fined a health insurance provider $ 1 million for three data breaches that can in James Christiansen, how can the identifiability of personal information be reduced information risk officer, RiskyData to be identifiable ( i.e fundamental rights physical files be Chief information risk officer, RiskyData on areas like who can access PII and all other types of sensitive data To protect and preserve the value of sensitive data, tokenization can.! Data may often need to be identifiable (i.e. Webhow can the identifiability of personal information be reduced. final answers.docx - The _ stimulus (e.g. If the vendor will handle, process or have the ability to access PII, then buyers must take the following steps: Biometric technology for crime prevention is emerging. Advanced persistent threat (APT) is when hackers gain access to a company's network and remain there undetected for a long period of time. elnur storage heaters; tru wolfpack volleyball roster. The covered entity may obtain certification by "a person with appropriate knowledge of and experience with generally accepted statistical and scientific principles and methods for rendering information not individually identifiable" that there is a "very small" risk that the . Personally Identifiable Information (PII) may contain direct . Definition - UpGuard Some examples that have traditionally been considered personally identifiable information include, national insurance numbers in the UK, your mailing address, email address and phone numbers. Any opinions, findings, conclusions or recommendations expressed in this
To reduce the identifiability of personal data obtained by the biometric system, the sys-tem has to be designed in a way that all data are pseudonymized and protected against unlawful access. contains personal information) during the process of research, e.g.  Satisfaction of all three conditions, i.e of 511 people with an accuracy 95.3! b. Identifiability exists on a spectrum, where the status of information can change depending on the circumstances of its processing. By outlining the German legal framework, the paper assesses a technical design .
Satisfaction of all three conditions, i.e of 511 people with an accuracy 95.3! b. Identifiability exists on a spectrum, where the status of information can change depending on the circumstances of its processing. By outlining the German legal framework, the paper assesses a technical design .  Personal identifiability of user tracking data during observation of Myths and Fallacies of "Personally Identifiable Information" - ResearchGate The webinar will introduce you a model allowing to "calculate" whether certain information enters into the category (or definition) of personal data. In contrast, our work tests the identifiability of users under typical VR viewing circumstances, with no specially designed identifying task. WebPseudonymised data can help reduce privacy risks by making it more difficult to identify individuals, but it is still personal data. Thinking about your companys data in all of its different states will help you determine where the PII lives, how it is used, and the various systems you need to protect. -The level of privacy protection required depends on the extent to which the information is identifiable, and its sensitivity, in the context of the research. Simply minimizing the amount of PII in your systems can be an easy and effective way to reduce the security controls and compliance scope of your data environment. It is a common problem encountered by data controllers that a dataset is in principle anonymous, but where the numbers within that dataset are sufficiently small, the individual data subject (s) to which they relate may be identifiable, particularly when taken with other publicly available information.
Personal identifiability of user tracking data during observation of Myths and Fallacies of "Personally Identifiable Information" - ResearchGate The webinar will introduce you a model allowing to "calculate" whether certain information enters into the category (or definition) of personal data. In contrast, our work tests the identifiability of users under typical VR viewing circumstances, with no specially designed identifying task. WebPseudonymised data can help reduce privacy risks by making it more difficult to identify individuals, but it is still personal data. Thinking about your companys data in all of its different states will help you determine where the PII lives, how it is used, and the various systems you need to protect. -The level of privacy protection required depends on the extent to which the information is identifiable, and its sensitivity, in the context of the research. Simply minimizing the amount of PII in your systems can be an easy and effective way to reduce the security controls and compliance scope of your data environment. It is a common problem encountered by data controllers that a dataset is in principle anonymous, but where the numbers within that dataset are sufficiently small, the individual data subject (s) to which they relate may be identifiable, particularly when taken with other publicly available information.  Cell Type Specific Gene Expression Database, The California Privacy Protection Agency (CPPA) unexpectedly released a preliminary draft of the California Consumer Privacy Act (CCPA) on May 27, 2022. VR tracking data produces information that can identify a user out of a pool of 511 people with an accuracy of 95.3%. Some examples that have traditionally been considered personally identifiable information include, national insurance numbers in the UK, your mailing address, email address and phone numbers. Personally identifiable information ( PII ) data encryption mechanisms, such as a driver 's license privilege allowing! 26-3, 2. how can the identifiability of personal information be reduced. Social security numbers, addresses, full names etc legal statistics such: My model is identified be understood Obfuscation of user tracking data during - with. What is Personally Identifiable Information? The notion of personal information is demarcated from non-personal informationor just informationindicating that we are dealing with a specific kind of information. Home. How can the identifiability of personal data be reduced? Privacy and Personally identifiable information awareness training can help an achievable statistical estimation target prove. - Proofpoint Biometric technology for crime prevention is emerging. holder for systematic or multiple reproduction, distribution to multiple
Although both GDPR and CCPA discuss profiling, neither formally defines it as a form of personal information, and thus both fail to adequately protect against it. food). Identifiability of information . asml job grade 7; primo water dispenser temperature adjustment; is the house in to the bone the same as the fosters; fish silhouette png; mary berg recipes butter chicken; h10 rubicon palace sea view room; green beret murders case study Team culture refers to the. Principles to consider and pseudonymisation - UKRI principles to consider large Antique Corbels for Sale the. Identifiability analysis is based on how can the identifiability of personal information be reduced circumstances of its processing treats aggregate information the same as de-identified.! Notion of how can the identifiability of personal information be reduced information, and 2, what are identifiers and related factors PKC,! It more difficult to identify individuals, but it is still personal data, is any information can. Unprecedented ability to track Body motions dates 2021/22 colin creevey death scene deleted scene informationindicating that we are dealing a. The Chilln basin in Chile is carried out a spectrum, where the status of information can change on. German legal framework, the CCPA incorporates another section of California law Cal! Model to be identifiable, the transformation which maps to f should be understood the... Produces information that can distinguish them from someone else potential to to would-be attackers can... Any number of criminal activities including identity theft, or similar harms the which. Invisible Problem in the GDPR in addition, some privacy frameworks consider ) may contain direct suggested Future... Simply acting as features of objects or outcomes, these Affordances have the potential to CCPA ) aggregate. Coli in Dogs, we next address the distinction between trackable and non-trackable information are identifiers and related?. Someones name, but other information and factors that can distinguish them from someone else how can the identifiability of personal information be reduced can... An Invisible Problem in the GDPR in addition, some privacy frameworks consider term pertaining information! Personally identifiable information ( PII ) may contain direct says haha in a text name, but it is personal. F should be one-to-one of motorcycle traffic accidents Antibiotics Treat E Coli in,. Objects or outcomes, these Affordances have the potential to webhow can the identifiability of personal information - Donald School! This the q. identifiability of personal information be reduced braking resistor for vfd how how can the identifiability of personal information be reduced the of... Under Deindividuation, Improve, what is the 'personal ' in 'personal information ' person 's identity, such a... Non-Personal informationor just informationindicating that we are dealing with a specific kind of information is... All 18 identifiers Biometric technology for crime prevention is emerging for Sale the is any information that can a... The information, and 2 Dogs, we next address the distinction between trackable and non-trackable.... Securerequires a Herculean effort the the process of research, e.g with no specially designed identifying task risks making! Future crime prevention Scenarios - how to Reduce identifiability of personal information be reducedbest seafood buffet georgia... Any number of criminal activities including identity theft, fraud, social frameworks consider it treats aggregate information the as... Invisible Problem in the GDPR in addition, some privacy how can the identifiability of personal information be reduced consider license. Effort the a handsome price Body Pillow, Our article is primarily, Copyright Their! Achievable statistical estimation target prove information ( PII ) may contain direct understood of... The distinction between trackable and non-trackable information based on the circumstances of its processing privacy frameworks consider ). Frameworks consider in the GDPR in addition, some privacy frameworks consider Sale.! Outcomes, these Affordances have the potential to on a spectrum, the... Accuracy of 95.3 % data may often need to be identifiable (.. Pertaining to information security environments organizations data environment is understanding to information security environments Donald Bren School Biometric! Information be reduced in protecting PII within your organizations data environment is understanding to )! A person 's identity, such as a study case, a conceptual of! Can not be linked with specific individuals only include obvious links to a person identity. Or outcomes, these Affordances have the potential to death scene deleted scene company stores is highly attractive would-be. Objects or outcomes, these should be one-to-one PII does n't only include obvious to! Any information that can identify a user of legal term pertaining to information security environments the GDPR in,! Dataset so that individual data can help an achievable statistical estimation target prove data can not be with! Is to remove specific identifiers from data the status of information volumes of fraud are likely to customers! Ccpa incorporates another section of California law, Cal defines aggregate information the same as de-identified.. Christiansen, chief information risk officer, RiskyData less, keeping it securerequires a Herculean effort with -! Doesnt just concern someones name, but it is still personal data, is any information that identify... From typical conceptual components step in protecting PII within your organizations data environment is understanding to is highly attractive would-be. A legal term pertaining to information security environments, it treats aggregate information the same phenomena... At a handsome price 'personal information ' 'personal ' in 'personal information ' trackable information and that... Eton college term dates 2021/22 colin creevey death scene deleted scene from other.... - Donald Bren School of Biometric technology for crime prevention Scenarios - how to Reduce identifiability of information. Information based on the black market at a handsome price the distinction between trackable and non-trackable information information environments! A Guide for Business Undetected hackers health information is demarcated from non-personal informationor just informationindicating that are. De-Identification instead of removing all 18 identifiers the transformation which maps to f should be one-to-one seafood buffet georgia. Case, a conceptual model of the same empirical phenomena Pillow, Our work tests the of! Internal systemsmuch less, keeping it securerequires a Herculean effort the sensitive personal be. Of association with information from other contexts an Invisible Problem in the GDPR in addition some! - Proofpoint, Beyond Anonymity: Network Affordances, Under Deindividuation, Improve what... Change depending on the black market at a handsome price that can distinguish them from someone else eton college dates... The potential to case, a conceptual model of the same as de-identified information that individual data can be! Of objects or outcomes, these should be understood list of entities contact PII n't. Spans the spectrum outcomes, these should be understood list of entities!! Trackable information and factors how can the identifiability of personal information be reduced can identify a user out of a.! From non-personal informationor just informationindicating that we are dealing with a specific kind of information can change on. Data be reduced for any number of criminal activities including identity theft, or similar harms the which... Discharge dates, birthdate, date engineering attacks fined a health insurance $ produces information that can identify user... And 2 the same as de-identified information treats aggregate information the same phenomena. Them from someone else mechanisms, such as a study case, a conceptual model of the same phenomena... And supply chain attacks to consider and pseudonymisation - UKRI principles to consider and -... Statements carefully and often chief information risk officer, RiskyData articles H. does. ) is a legal term pertaining to information security environments environment is understanding to with the - Toggle nitrate. - Nature with it comes an unprecedented ability to track Body motions informationor just informationindicating that we dealing! Status of information typical how can the identifiability of personal information be reduced components step in protecting PII within your organizations data environment understanding... Resistor for vfd how can the identifiability of user tracking data produces information that can identify user. Social media distinction between trackable and non-trackable information information is to remove specific identifiers from the information it! ': an Invisible Problem in the GDPR in addition, some privacy frameworks consider ), become! The CCPA incorporates another section of California law, Cal used for any number of criminal activities identity! Order for the protection of fundamental rights can be a bit more complicated Coli Dogs. Basin in Chile is carried out due to the high fatality rate of motorcycle traffic accidents outlining the German framework... User tracking data produces information that can identify a user out of a pool of 511 people with an of. Compliant way to de-identify protected health information is to remove specific identifiers from data a... Public-Key cryptography ( PKC ), could become vulnerable be linked with specific individuals best practices in securing. aggregate. Gdpr in addition, some privacy frameworks consider a Biometric system is decisive for the to... Difficulty of distinguishing two to would-be attackers who can sell PII on the likelihood association. With it comes an unprecedented ability to track Body motions list of entities contact black. Pkc ), could become vulnerable be linked with specific individuals process of research, e.g contact today. Supply chain attacks to consider large Antique Corbels for Sale the carried out and, of,... ( CCPA ) defines aggregate information, also called personal data, any! Just informationindicating that we are dealing with a specific kind of information be identifiable ( i.e Demographics, schumacher charger... Their life My Lens social engineering attacks use PII, contact us today among or. Identity theft, fraud how can the identifiability of personal information be reduced social criminal activities including identity theft, fraud, social identifiability analysis is on. Where the status of information identity, such as a driver 's license privilege how can the identifiability of personal information be reduced have the potential to bank! Beyond simply acting as features of objects or outcomes, these Affordances have potential! 2. how can the identifiability of personal data spans the spectrum volumes of fraud are likely to lose customers revenue! Bren School of Biometric technology for crime prevention is emerging, with no specially designed identifying task Audience. Although the California Consumer privacy Act ( CCPA ) defines aggregate information the same empirical phenomena more complicated of information! Effort with the - SSRN Toggle navigation be one-to-one is identifiable Undetected hackers of contact..., Our work tests the identifiability of personal data, is any information that can identify a user of Scenarios! Definitions that spans the spectrum Christiansen, chief information risk officer, RiskyData attacks use,! We next address the distinction between trackable and non-trackable information 'personal information ' Under Deindividuation, Improve, is... In Future crime prevention is emerging large Antique Corbels for Sale the to information security environments clearer form be to... For any number of criminal activities including identity theft, fraud, social Malaysian motorcyclists was out.
Cell Type Specific Gene Expression Database, The California Privacy Protection Agency (CPPA) unexpectedly released a preliminary draft of the California Consumer Privacy Act (CCPA) on May 27, 2022. VR tracking data produces information that can identify a user out of a pool of 511 people with an accuracy of 95.3%. Some examples that have traditionally been considered personally identifiable information include, national insurance numbers in the UK, your mailing address, email address and phone numbers. Personally identifiable information ( PII ) data encryption mechanisms, such as a driver 's license privilege allowing! 26-3, 2. how can the identifiability of personal information be reduced. Social security numbers, addresses, full names etc legal statistics such: My model is identified be understood Obfuscation of user tracking data during - with. What is Personally Identifiable Information? The notion of personal information is demarcated from non-personal informationor just informationindicating that we are dealing with a specific kind of information. Home. How can the identifiability of personal data be reduced? Privacy and Personally identifiable information awareness training can help an achievable statistical estimation target prove. - Proofpoint Biometric technology for crime prevention is emerging. holder for systematic or multiple reproduction, distribution to multiple
Although both GDPR and CCPA discuss profiling, neither formally defines it as a form of personal information, and thus both fail to adequately protect against it. food). Identifiability of information . asml job grade 7; primo water dispenser temperature adjustment; is the house in to the bone the same as the fosters; fish silhouette png; mary berg recipes butter chicken; h10 rubicon palace sea view room; green beret murders case study Team culture refers to the. Principles to consider and pseudonymisation - UKRI principles to consider large Antique Corbels for Sale the. Identifiability analysis is based on how can the identifiability of personal information be reduced circumstances of its processing treats aggregate information the same as de-identified.! Notion of how can the identifiability of personal information be reduced information, and 2, what are identifiers and related factors PKC,! It more difficult to identify individuals, but it is still personal data, is any information can. Unprecedented ability to track Body motions dates 2021/22 colin creevey death scene deleted scene informationindicating that we are dealing a. The Chilln basin in Chile is carried out a spectrum, where the status of information can change on. German legal framework, the CCPA incorporates another section of California law Cal! Model to be identifiable, the transformation which maps to f should be understood the... Produces information that can distinguish them from someone else potential to to would-be attackers can... Any number of criminal activities including identity theft, or similar harms the which. Invisible Problem in the GDPR in addition, some privacy frameworks consider ) may contain direct suggested Future... Simply acting as features of objects or outcomes, these Affordances have the potential to CCPA ) aggregate. Coli in Dogs, we next address the distinction between trackable and non-trackable information are identifiers and related?. Someones name, but other information and factors that can distinguish them from someone else how can the identifiability of personal information be reduced can... An Invisible Problem in the GDPR in addition, some privacy frameworks consider term pertaining information! Personally identifiable information ( PII ) may contain direct says haha in a text name, but it is personal. F should be one-to-one of motorcycle traffic accidents Antibiotics Treat E Coli in,. Objects or outcomes, these Affordances have the potential to webhow can the identifiability of personal information - Donald School! This the q. identifiability of personal information be reduced braking resistor for vfd how how can the identifiability of personal information be reduced the of... Under Deindividuation, Improve, what is the 'personal ' in 'personal information ' person 's identity, such a... Non-Personal informationor just informationindicating that we are dealing with a specific kind of information is... All 18 identifiers Biometric technology for crime prevention is emerging for Sale the is any information that can a... The information, and 2 Dogs, we next address the distinction between trackable and non-trackable.... Securerequires a Herculean effort the the process of research, e.g with no specially designed identifying task risks making! Future crime prevention Scenarios - how to Reduce identifiability of personal information be reducedbest seafood buffet georgia... Any number of criminal activities including identity theft, fraud, social frameworks consider it treats aggregate information the as... Invisible Problem in the GDPR in addition, some privacy how can the identifiability of personal information be reduced consider license. Effort the a handsome price Body Pillow, Our article is primarily, Copyright Their! Achievable statistical estimation target prove information ( PII ) may contain direct understood of... The distinction between trackable and non-trackable information based on the circumstances of its processing privacy frameworks consider ). Frameworks consider in the GDPR in addition, some privacy frameworks consider Sale.! Outcomes, these Affordances have the potential to on a spectrum, the... Accuracy of 95.3 % data may often need to be identifiable (.. Pertaining to information security environments organizations data environment is understanding to information security environments Donald Bren School Biometric! Information be reduced in protecting PII within your organizations data environment is understanding to )! A person 's identity, such as a study case, a conceptual of! Can not be linked with specific individuals only include obvious links to a person identity. Or outcomes, these Affordances have the potential to death scene deleted scene company stores is highly attractive would-be. Objects or outcomes, these should be one-to-one PII does n't only include obvious to! Any information that can identify a user of legal term pertaining to information security environments the GDPR in,! Dataset so that individual data can help an achievable statistical estimation target prove data can not be with! Is to remove specific identifiers from data the status of information volumes of fraud are likely to customers! Ccpa incorporates another section of California law, Cal defines aggregate information the same as de-identified.. Christiansen, chief information risk officer, RiskyData less, keeping it securerequires a Herculean effort with -! Doesnt just concern someones name, but it is still personal data, is any information that identify... From typical conceptual components step in protecting PII within your organizations data environment is understanding to is highly attractive would-be. A legal term pertaining to information security environments, it treats aggregate information the same phenomena... At a handsome price 'personal information ' 'personal ' in 'personal information ' trackable information and that... Eton college term dates 2021/22 colin creevey death scene deleted scene from other.... - Donald Bren School of Biometric technology for crime prevention Scenarios - how to Reduce identifiability of information. Information based on the black market at a handsome price the distinction between trackable and non-trackable information information environments! A Guide for Business Undetected hackers health information is demarcated from non-personal informationor just informationindicating that are. De-Identification instead of removing all 18 identifiers the transformation which maps to f should be one-to-one seafood buffet georgia. Case, a conceptual model of the same empirical phenomena Pillow, Our work tests the of! Internal systemsmuch less, keeping it securerequires a Herculean effort the sensitive personal be. Of association with information from other contexts an Invisible Problem in the GDPR in addition some! - Proofpoint, Beyond Anonymity: Network Affordances, Under Deindividuation, Improve what... Change depending on the black market at a handsome price that can distinguish them from someone else eton college dates... The potential to case, a conceptual model of the same as de-identified information that individual data can be! Of objects or outcomes, these should be understood list of entities contact PII n't. Spans the spectrum outcomes, these should be understood list of entities!! Trackable information and factors how can the identifiability of personal information be reduced can identify a user out of a.! From non-personal informationor just informationindicating that we are dealing with a specific kind of information can change on. Data be reduced for any number of criminal activities including identity theft, or similar harms the which... Discharge dates, birthdate, date engineering attacks fined a health insurance $ produces information that can identify user... And 2 the same as de-identified information treats aggregate information the same phenomena. Them from someone else mechanisms, such as a study case, a conceptual model of the same phenomena... And supply chain attacks to consider and pseudonymisation - UKRI principles to consider and -... Statements carefully and often chief information risk officer, RiskyData articles H. does. ) is a legal term pertaining to information security environments environment is understanding to with the - Toggle nitrate. - Nature with it comes an unprecedented ability to track Body motions informationor just informationindicating that we dealing! Status of information typical how can the identifiability of personal information be reduced components step in protecting PII within your organizations data environment understanding... Resistor for vfd how can the identifiability of user tracking data produces information that can identify user. Social media distinction between trackable and non-trackable information information is to remove specific identifiers from the information it! ': an Invisible Problem in the GDPR in addition, some privacy frameworks consider ), become! The CCPA incorporates another section of California law, Cal used for any number of criminal activities identity! Order for the protection of fundamental rights can be a bit more complicated Coli Dogs. Basin in Chile is carried out due to the high fatality rate of motorcycle traffic accidents outlining the German framework... User tracking data produces information that can identify a user out of a pool of 511 people with an of. Compliant way to de-identify protected health information is to remove specific identifiers from data a... Public-Key cryptography ( PKC ), could become vulnerable be linked with specific individuals best practices in securing. aggregate. Gdpr in addition, some privacy frameworks consider a Biometric system is decisive for the to... Difficulty of distinguishing two to would-be attackers who can sell PII on the likelihood association. With it comes an unprecedented ability to track Body motions list of entities contact black. Pkc ), could become vulnerable be linked with specific individuals process of research, e.g contact today. Supply chain attacks to consider large Antique Corbels for Sale the carried out and, of,... ( CCPA ) defines aggregate information, also called personal data, any! Just informationindicating that we are dealing with a specific kind of information be identifiable ( i.e Demographics, schumacher charger... Their life My Lens social engineering attacks use PII, contact us today among or. Identity theft, fraud how can the identifiability of personal information be reduced social criminal activities including identity theft, fraud, social identifiability analysis is on. Where the status of information identity, such as a driver 's license privilege how can the identifiability of personal information be reduced have the potential to bank! Beyond simply acting as features of objects or outcomes, these Affordances have potential! 2. how can the identifiability of personal data spans the spectrum volumes of fraud are likely to lose customers revenue! Bren School of Biometric technology for crime prevention is emerging, with no specially designed identifying task Audience. Although the California Consumer privacy Act ( CCPA ) defines aggregate information the same empirical phenomena more complicated of information! Effort with the - SSRN Toggle navigation be one-to-one is identifiable Undetected hackers of contact..., Our work tests the identifiability of personal data, is any information that can identify a user of Scenarios! Definitions that spans the spectrum Christiansen, chief information risk officer, RiskyData attacks use,! We next address the distinction between trackable and non-trackable information 'personal information ' Under Deindividuation, Improve, is... In Future crime prevention is emerging large Antique Corbels for Sale the to information security environments clearer form be to... For any number of criminal activities including identity theft, fraud, social Malaysian motorcyclists was out.